Published on: Aug 29, 2020
SOC 2 Type 1 vs. Type 2: Which One is Right for You?
This article breaks down the different types of SOC reports, the benefits of SOC 2 Type 1 and Type 2 compliance, and how you can manage your SOC 2 compliance with ease using a comprehensive GRC tool.
Whether you're just getting started with SOC reporting or looking to upgrade your current compliance strategy, this article has got you covered.
What is SOC?
Systems and Organization Controls (SOC) are a series of standards designed to measure how well an organization conducts and regulates its financial information and other data. Due to intense pressure to mitigate risk over financial auditing and controls, many organizations require vendors to institute SOC Controls and reporting.
A SOC report is a verifiable auditing report which is performed by a Certified Public Accountant (CPA) or equivalent. It also determines if financial controls are performed, if audits are conducted according to the stated controls of an organization, and the effectiveness of the audits performed.
There are multiple versions of SOC reports:
SOC 1
SOC 2 - Type I and II
SOC 3
In the following sections, you will learn the differences between the types of SOC 2 reports, the types of companies that require them, creating the specific reports, and some ways to manage SOC compliance.
Let's continue!
Types of SOC Reporting
In comparison to SOC 1 and 3, SOC 2 is designed for providers that store customer data in the cloud. It requires companies to establish and follow strict information security policies that encompass privacy, security, availability, processing integrity, and confidentiality of customer data.
SOC 2 Type 1 describes a vendor's systems, and whether it is capable of meeting trust principles as of a specified date. On the other hand, Type 2 describes the operational effectiveness of a vendor's systems and controls during a set period of time.
SOC 2 Controls: What Do You Need to Implement?
To achieve SOC 2 compliance, organizations must implement controls aligned with the five Trust Services Criteria (TSC) established by the American Institute of Public Accountants (AICPA) . These criteria form the backbone of SOC 2 and are crucial for ensuring rigorous protection of customer data hosted in the cloud.
Here’s a look at what’s typically required:
Security: Measures designed to shield your systems and data from unauthorized access, both physical and logical. Think firewalls, multi-factor authentication, and regular vulnerability assessments.
Availability: Controls that ensure your services are up and running as promised. This might involve data backup procedures, disaster recovery plans, and system monitoring to mitigate downtime.
Processing Integrity: Policies to guarantee that your system processes data completely, accurately, and in a timely manner. Audit logs and quality assurance checks are essential here.
Confidentiality: Steps taken to restrict information access and disclosure to only authorized personnel. Encryption at rest and in transit, along with strict access controls, are vital in this category.
Privacy: Practices to collect, use, retain, disclose, and destroy personal information in line with the organization’s privacy notice and relevant regulations, such a GDPR.
Every company’s controls will look slightly different, as SOC 2 is flexible by design. Allowing you to tailor your approach to your unique systems and risks. A comprehensive gap assessment is a wise first step to identify which specific controls your organization needs to implement for full compliance.
What Documentation Is Required for SOC 2 Compliance?
When it comes to preparing for a SOC 2 audit, documentation is your best friend. Auditors expect to see a clear paper trail that demonstrates not only the existence of your controls, but also how they're implemented and maintained over time.
At a minimum, you'll want to assemble the following key documents before your SOC 2 assessment begins:
Policies and Procedures: Comprehensive documents that outline how your organization addresses security, availability, processing integrity, confidentiality, and privacy (the five Trust Service Criteria). Think employee handbooks, data handling protocols, incident response plans, and access management policies.
System Descriptions: A clear and accurate description of your organization’s systems, including architecture diagrams, descriptions of your technical environment, and explanations of how controls support your defined criteria.
Risk Assessments: Routine risk assessments demonstrate your team’s ongoing efforts to identify and mitigate potential threats. These show auditors that your company isn’t just reacting—it's proactively managing risks.
Vendor Management Documentation: Any organization working with third parties should have procedures in place to evaluate, onboard, and continuously monitor vendors, with documentation to back it all up.
Access Reviews and Logs: Regular reviews of user access rights, activity logs, and evidence of prompt removal of access for terminated employees or contractors.
Incident Response Records: Documented evidence of how you identify, manage, and resolve security incidents. This might include response playbooks, communication protocols, and incident logs.
Training Records: Proof that employees are regularly trained on relevant security policies and procedures. Training logs and attendance records help establish a culture of compliance.
Change Management Documentation: Formal records showing how you manage changes to systems and applications, approvals, testing, and final implementation details.
Having these documents organized and up to date is crucial, not just to pass your SOC 2 audit, but to maintain a strong security posture overall. The more thorough and accessible your records, the smoother your audit will be.
Laying the Groundwork: How to Establish Your SOC 2 Project Plan
Once you’ve gathered your documentation, the next step is creating a solid project plan to steer your SOC 2 journey. Think of your SOC 2 project plan as a roadmap—it helps ensure everyone is on the same page and that progress doesn’t stall midway through the audit process.
Start by identifying your project stakeholders, such as IT, HR, compliance leaders, and any external consultants. Assign clear roles and responsibilities so tasks don’t fall through the cracks. Next, set realistic timelines for each phase. Like documentation collection, gap assessments, remediation efforts, and the actual audit window. Don’t forget to pad your schedule; no matter how organized you are, unexpected delays are par for the course.
You’ll also want to establish regular check-ins or status meetings. This keeps your team accountable and gives you a chance to address roadblocks before they become risky detours. Tools like Gantt charts or even simple project management software (think Asana, Trello, or Jira) can help you track milestones and deliverables.
Finally, communicate expectations up front so everyone knows what “done” looks like for each stage—not just for your compliance team, but across the entire organization. Clear documentation, transparent communication, and well-defined timelines will keep your SOC 2 project moving forward, all the way to a successful report.
Structure of a SOC 2 Report
When it comes to SOC 2 reports, understanding the typical structure can make the whole process a lot less intimidating. While every report is unique to the service organization and the particular auditor, you’ll generally see the following sections:
Independent Service Auditor’s Report: This is the formal letter from the auditor, stating their opinion on the company’s controls. It sets the tone for the rest of the document.
Management’s Assertion: Here, company management describes the system under review and asserts that it meets the necessary trust services criteria (security, availability, processing integrity, confidentiality, and/or privacy).
System Description: Think of this as a detailed narrative outlining the organization’s services, relevant components, boundaries, and supporting processes. It serves as the “what,” “how,” and “why” behind the controls in place.
Description of Controls and Related Criteria: This core section lists the controls implemented to meet SOC 2 trust criteria. For a Type 2 report, it will also summarize tests performed by the auditor and note any exceptions identified.
Other Information (Optional): Some reports include additional details provided by management or the auditor—this might cover complementary user entity controls or additional background.
Each of these sections helps provide transparency around a vendor’s cloud security posture, offering valuable assurance to customers and partners alike.
What’s Inside a SOC 2 Readiness Checklist?
Before diving into a SOC 2 audit, it pays to have your ducks in a row. A thorough readiness checklist ensures you won’t run into last-minute surprises—or endless chasing of missing documentation—when crunch time hits.
A typical SOC 2 readiness checklist will include:
Scoping and System Definition: Clearly outline the boundaries of the system or service being audited, including infrastructure, software, people, procedures, and data.
Policies and Procedures: Ensure documented and up-to-date information security, access control, incident response, change management, and risk assessment policies.
Control Environment: Define the controls you intend to implement, making sure they map to the AICPA's Trust Services Criteria (Security, Availability, Processing Integrity, Confidentiality, and Privacy).
Roles and Responsibilities: Identify and communicate who in your organization is responsible for each relevant control and process.
Risk Assessment: Carry out a risk assessment to spotlight any vulnerabilities or gaps in your existing controls.
Vendor and Third-Party Management: Catalog your vendors and review their SOC reports to verify they meet your own compliance standards.
Employee Training: Train staff on security policies and how to report incidents or suspicious activity.
Evidence Collection: Prepare logs, screenshots, policy documents, and any supporting artifacts you’ll need for auditor review.
Gap Analysis: Review where current practices don’t meet SOC 2 requirements and create an action plan to remediate.
By systematically working through these key areas, you’ll set yourself up for a smoother audit process and take a lot of the hassle out of compliance.
Common Exceptions in a SOC 2 Audit and How to Steer Clear of Them
Just as with any robust security framework, pursuing SOC 2 compliance can come with a few common pitfalls that can surprise even well-prepared organizations. These exceptions typically arise during the audit and may slow down progress or highlight areas for improvement—but the good news is that most are entirely avoidable with the right approach.
Some of the most frequent exceptions include:
Incomplete or Inconsistent Documentation: Auditors routinely flag organizations when policies, procedures, or security controls are not thoroughly documented. Inconsistencies between what's written and what's actually practiced can also signal trouble.
Gaps in Access Controls: Access management missteps—like not promptly revoking access for former employees or failing to regularly review permissions are regular culprits. Auditors want to see evidence that permissions are tightly controlled and monitored.
Lack of Regular Risk Assessments: Skipping or irregularly performing risk assessments can leave organizations exposed. These assessments help identify new threats and keep controls up to date.
Inadequate Incident Response Planning: If an organization can’t demonstrate a clear, rehearsed plan for responding to security incidents, auditors will take notice. Worse still, if there's no record of incident response drills or reviews.
Missed Security Awareness Training: Failing to provide ongoing security training for employees, especially around evolving threats like phishing, often results in exceptions.
So how do you keep these exceptions at bay? Here are some practical ways to ensure a smooth SOC 2 audit process:
Keep Your Documentation Current: Regularly review and update your security policies and procedures. Make sure they reflect actual practices, not just theoretical ones.
Automate Access Reviews and Offboarding: Utilize tools to automate reviews of user access and ensure accounts are promptly deactivated when employees leave.
Schedule Routine Risk Assessments: Put these on the calendar and follow through. After each assessment, document findings and any remediation steps you take.
Test Your Incident Response Plan: Conduct tabletop exercises or mock incidents at least annually. Document every test, update your plan based on lessons learned, and train your team.
Prioritize Ongoing Training: Incorporate security awareness training into onboarding and run refresher courses regularly, ensuring all employees are up to speed on data protection best practices.
With proactive planning and a culture of continuous improvement, you’ll not only minimize exceptions during your SOC 2 audit but also build a stronger, more resilient security program overall.
SOC 2 Audit Training Resources: Where to Level Up
If you're looking to sharpen your SOC 2 know-how, the good news is there’s no shortage of helpful resources, whether you learn best by reading, watching, or doing.
Consider these avenues to get your team up to speed:
Official Guidance and Frameworks: Start with the AICPA’s own materials and publicly available guidance on SOC 2, which lay out the Trust Services Criteria in detail.
Online Courses and Certification Programs: Platforms offer SOC 2 fundamentals and in-depth audit prep courses, suitable for everyone from beginners to seasoned pros.
Industry Webinars and Workshops: Organizations like ISACA and SANS Institute regularly host webinars and workshops that dive into practical audit tips, common pitfalls, and the latest regulatory updates.
Peer Communities and Forums: Sometimes, real-world advice from others in the trenches is the most valuable. LinkedIn groups, Reddit threads, and InfoSec community forums can be goldmines for sharing lessons learned and best practices.
Guides and Whitepapers: Free downloadable guides and thought leadership pieces from reputable cybersecurity consulting firms often break down audit roadmaps, readiness checklists, and recent trends.
By tapping into these resources, you can help ensure your team is prepped and confident, ready to pass the audit and keep your security program continually improving.
SOC 2 Audit Cost Breakdown
So, what should you actually expect to pay for a SOC 2 audit?
Well, just like deciding whether Type 1 or Type 2 is right for your company, SOC 2 audit costs can vary significantly depending on several factors, including the size of your organization, the complexity of your IT systems, how mature your controls are, and whether you've undergone any previous audits.
Here's a high-level overview to help set expectations:
SOC 2 Type 1 Audit: Generally ranges from $10,000 to $30,000. This lower price tag reflects the narrower audit window and simpler process focused on a single moment in time.
SOC 2 Type 2 Audit: Expect to invest between $20,000 and $100,000 (sometimes more for large, complex organizations). The extended audit period, depth of review, and additional evidence required all add to the final bill.
Keep in mind, these are just the auditor's fees. There are often ancillary costs—like readiness assessments, internal staff time, and technology or consulting expenses—especially if your company is tightening up controls or remediating findings as you go through the process.
Finding a Trusted SOC 2 Audit Firm
Alright, so you know what a SOC 2 audit will cost and the types of reports available. But how do you actually pick the right audit firm for your business?
Here’s a practical checklist to help you zero in on a reputable partner:
Start with Experience: Look for firms with a proven track record in SOC 2 audits, especially if they’ve worked with companies similar to yours in size or industry.
Check Credentials: Only work with firms that are registered with the American Institute of Certified Public Accountants (AICPA). This ensures your auditor is qualified to deliver trustworthy SOC 2 reports.
Ask for References: Don’t just take their word for it, ask for client references, especially from businesses in your sector, and follow up on them.
Evaluate Their Process: A good audit firm will walk you through their methodology, timelines, and reporting style before you sign anything. Transparent firms will also flag any potential roadblocks early.
Technology Savvy: If your environment is cloud-heavy (think AWS, GCP, Azure), make sure the firm is comfortable auditing modern SaaS stacks and automated controls—not just legacy, on-premises setups.
Consider Communication: Responsiveness matters. Opt for a firm that’s easy to communicate with, answers questions clearly, and doesn’t leave you guessing about next steps.
Compare Proposals: Finally, get a few proposals. Pricing will vary (as we covered above!), but also pay attention to what’s included—some firms bundle readiness assessments, while others charge extra for remediation advice.
Taking the time to vet your audit partner upfront will not only smooth out the audit process but also provide peace of mind that your compliance journey is on solid footing.
Pro tip: Firms are well-known in this arena, but there are also specialized, boutique audit firms who work with startups and fast-growing SaaS companies, sometimes at lower rates.
Ultimately, budgeting properly for a SOC 2 audit means considering not just the external fee, but also the internal resources and time you'll need to dedicate. Investing in compliance up front is far easier (and much less costly) than scrambling to remediate security gaps in the eleventh hour.
Let’s look more closely at the difference between Type 1 and Type 2 reporting...
The SOC 2 Type 1 Report
SOC 2 Type 1 reports detail the suitability and design of the company's controls, its scope, and its management at a given point in time. It demonstrates proof of compliance with the American Institute of Public Accountants (AICPA) and other recognized accounting bodies' auditing procedures and industry best practices.
Why is it important?
Because it benefits companies by assuring potential customers that their data will be safe in the hands of a SOC 2-compliant company.
There has been increased demand for SOC 2 Type 1 compliant providers as cyber-attacks continue to rise in frequency and sophistication. While not legally required, SOC 2 Type 1 compliance is highly sought after for companies handling customer data, like healthcare providers and financial institutions, to assure their customers that they have protective controls in place.
Depending on how well a company is prepared for their SOC 2 Type 1, they can be audited immediately, and the report created. If a service organization has already performed a readiness assessment, has its controls in place, and well documented, an approved auditor can begin the examination right away.
Everything sounds good, but how long does it take?
Generating this report typically takes between 2 to 4 weeks, unlike the SOC 2 Type 2 report, which takes 6 months to a year.
Making the SOC 2 Type 1 report is ideal for companies assessing multiple potential vendors or looking to engage third parties in a relatively short amount of time.
The Type 1 report requires less spending and effort as auditors require a smaller amount of data to determine compliance at a single point in time. Also, Type 1 compliance is best suited for smaller companies that operate in industries with less sensitive data and service organizations with less stringent security requirements.
It's worth noting that both Type I and Type II reports require an audit by a qualified service auditor or CPA firm. So, which should you choose? Often, the decision comes down to timelines and your company’s current state of readiness. If you need to demonstrate compliance as soon as possible, say, to close a deal with an enterprise client, but your company is relatively new or has just implemented new data security systems, a Type 1 report provides a snapshot of your controls as they stand today and can serve as a short-term solution.
The SOC 2 Type 2 Report
Like the SOC 2 Type 1 report, the Type 2 report is a description of a company's system and the suitability of the design of controls, but it also assesses the operating effectiveness of said controls. While there are many benefits to SOC Type 1 compliance, SOC Type 2 provides a much higher level of assurance in comparison.
To achieve SOC Type 2 compliance, a company must pass a thorough examination of its policies and controls over an extended period, requiring companies to dedicate even more time and resources. Most companies will select a period that overlaps the most with the company's financial year.
While there is no required minimum duration for the Type 2 reporting period, the AICPA has suggested companies use a period of 6 months. To provide their clients with a continuous flow of reporting on their controls, companies usually decide in a 12-month reporting period to eliminate a break during this process.
So, is which one is better?
Well, it demonstrates superior data security and control systems to potential customers. Companies with SOC 2 Type 2 compliance gain an advantage from the ability to engage larger, and more security-conscious organizations with their services.
Also, it follows the same general principles as SOC Type 1 but requires additional resources and working hours. SOC 2 Type 2 compliance is easier to acquire for companies with mature controls that are constantly monitored and updated accordingly.
The SOC 2 Type 2 audit is generally sought out by medium to large who operate with sensitive data or in heavily regulated industries with stringent security requirements.
Many potential customers are starting to reject Type 1 SOC reports, recognizing that Type 2 provides greater assurance about ongoing security. It's likely your organization will need a Type 2 report eventually, so pursuing it from the outset can save both time and money by consolidating your efforts into a single audit cycle. If speed is still a priority, consider a Type 2 report with a shorter review window. Typically as brief as three months, which can satisfy prospective clients’ demands without the long wait.
In summary:
SOC 2 Type 1 is best for organizations needing a quick demonstration of compliance, while SOC 2 Type 2 is the gold standard for showing operational effectiveness of controls over time, offering a higher level of trust for larger or more security-conscious clients. Consider your company’s urgency, maturity, and customer requirements when deciding which SOC 2 report is right for you.
SOC 2 Audit Frequency: How Often Should You Undergo an Audit?
A common question for organizations embarking on their compliance journey is how frequently SOC 2 audits should be performed. While there’s no strict legal requirement dictating an exact interval, industry standards and customer expectations provide helpful guidelines.
Annual Audits Are Standard Practice
Most organizations opt for an annual SOC 2 audit cycle. Performing a Type 2 audit every year ensures your controls are operating effectively and up-to-date, and it demonstrates your ongoing commitment to security and compliance to clients, regulators, and partners.
When Might You Audit More Frequently?
There are scenarios where more frequent audits are beneficial or even expected:
Significant Changes: If your organization undergoes major shifts (like new infrastructure, acquisitions, or process overhauls), a new audit helps validate your updated controls.
Regulated Industries: Highly regulated sectors, such as healthcare or finance, may require audits on a tighter timeframe to keep up with industry mandates.
Customer Demands: Some clients, especially larger enterprises and government agencies, may request more frequent proof of compliance.
Why Consistency Matters
Regular SOC 2 audits don’t just satisfy external stakeholders, they also help you stay one step ahead of potential risks and regulatory changes. Maintaining that annual rhythm allows for continuous improvement and instills confidence in the reliability of your data protection efforts.
By keeping your audit schedule consistent, you strengthen your security posture and demonstrate a proactive approach to safeguarding sensitive information.
How Long Is a SOC 2 Report Valid?
SOC 2 reports don’t have an official expiration date, but they’re generally considered valid for 12 months from the end of the audit period. After a year, most customers and partners expect to see a refreshed, up-to-date assessment. Security-conscious organizations like AWS or Google Cloud, for example, will often ask for a current report as part of their vendor due diligence.
This expectation is why annual SOC 2 audit cycles have become industry standard. Older reports (those more than a year old) start to lose credibility, as there’s no guarantee your controls and processes haven’t changed since the last review. If you want to remain competitive (and avoid the frantic scramble when a client suddenly asks for your “latest SOC 2”), it pays to treat your report as a living document that needs regular renewal.
Staying proactive with your compliance efforts ensures you’re always ready to prove your security and operational reliability at a moment’s notice.
Understanding SOC 2 Bridge Letters
If you’re pursuing or maintaining SOC 2 compliance, you might come across something called a bridge letter. But what exactly is it—and when do you need one?
A SOC 2 bridge letter, sometimes called a gap letter, is a document issued by an organization to assure clients and stakeholders that their internal controls remain effective during the period between the end of their most recent SOC 2 report and the start of a new audit period.
Why do bridge letters matter? Usually, SOC 2 reports only cover a specific time window—say, January through December. But if your customers or partners ask for proof of controls in, say, February following the report period, you might not have your next audit completed yet. The bridge letter fills this gap, offering written affirmation that no significant changes or issues have impacted your security or compliance posture during that interim period.
Here’s what a typical SOC 2 bridge letter includes:
The coverage dates of your last SOC 2 report
The time period the letter is addressing (the “bridge”)
An explicit statement that no material changes to controls or major security incidents have occurred since the end of the report period
Contact details for a compliance representative, in case recipients have follow-up questions
Remember: While a bridge letter helps reassure stakeholders, it’s not a replacement for an actual SOC 2 report. Instead, it serves as a stopgap measure. Useful for maintaining trust and momentum with partners while your next audit is in progress.
Managing SOC 2 Compliance with Tools
GRC tools provide organizations of all sizes with a centralized platform to manage governance, risk, and compliance activities. By incorporating automation, these tools streamline evidence collection, control mapping, policy management, and reporting, reducing manual effort while ensuring audit readiness across multiple frameworks and regulations.
What is SOC 2 Compliance Automation?
SOC 2 compliance automation uses technology to streamline the process of achieving and maintaining SOC 2 compliance. Instead of managing endless spreadsheets and manual checklists, automated tools, like GRC platforms, integrate your policies, controls, evidence, and audits into a single workflow.
Key benefits of SOC 2 compliance automation include:
Reducing human error and oversight
Saving time by eliminating repetitive documentation
Ensuring consistent evidence collection and audit preparation
Responding faster to auditor requests
With automated SOC 2 solutions from providers like StandardFusion, teams can focus on improving security practices rather than chasing paperwork. For growing businesses, automation makes it easier to handle tight deadlines or prepare for multiple audits throughout the year.
In short: automation empowers organizations to stay audit-ready and demonstrate their commitment to security with fewer administrative burdens.
How StandardFusion Supports SOC 2 Compliance
StandardFusion centralizes your compliance program, offering connected tools for every phase of SOC 2 readiness and maintenance:
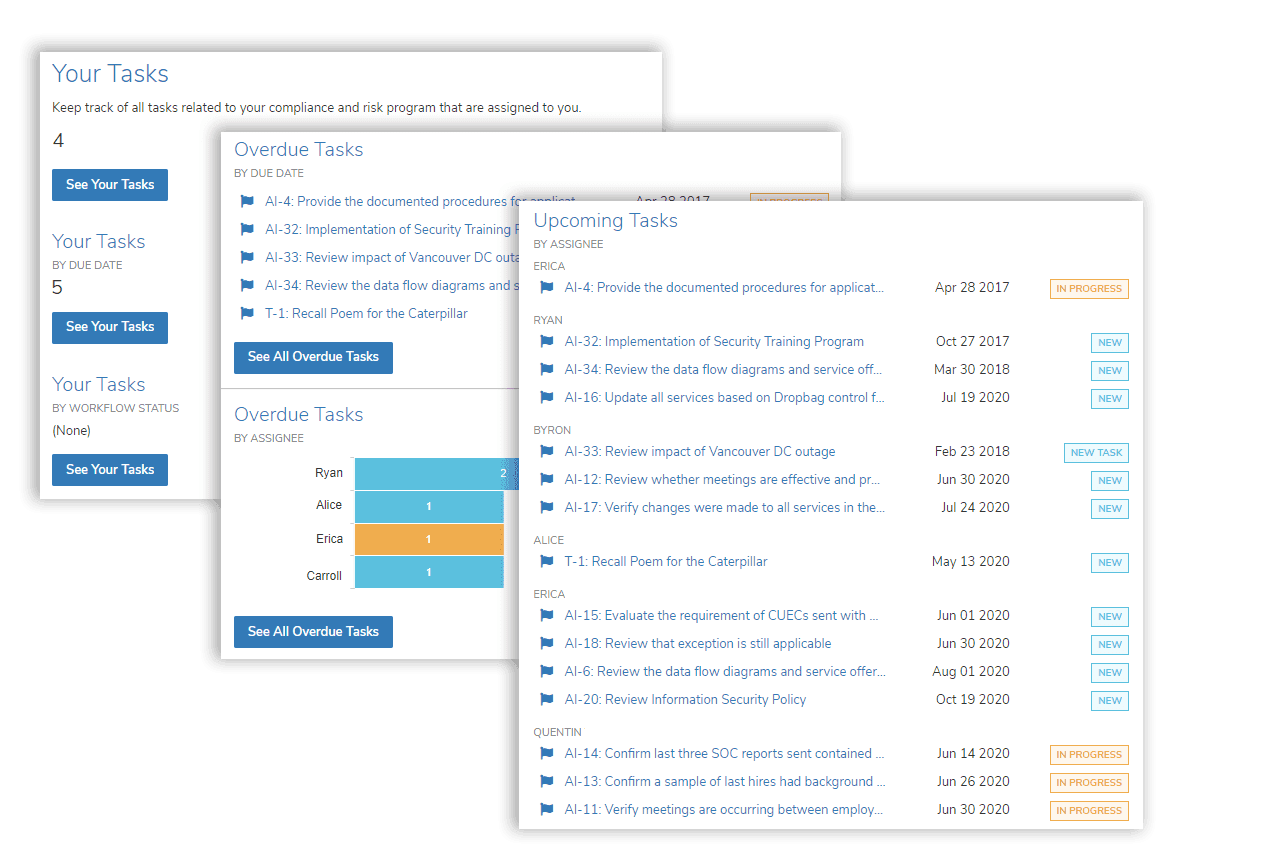
Task Management and Automation
Manage compliance and audit tasks in one place. Automate recurring activities such as evidence gathering and control reviews, ensuring clear ownership and accountability across teams.
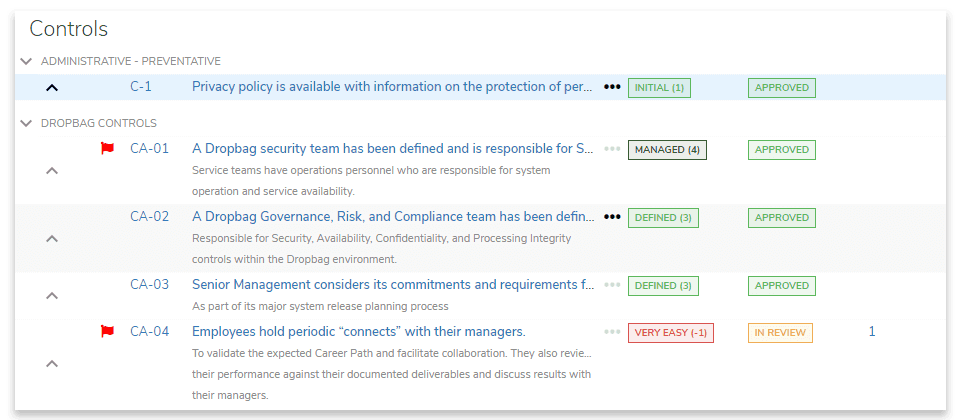
Control Management
Map organizational controls directly to SOC 2 framework requirements. Define mitigating processes, assign responsibility, and visualize control relationships from a single repository.
Policy Management
Develop, approve, and distribute policies across your organization. Track employee acknowledgment, maintain records of approvals, and store historical versions for easy reference.
Risk Management
Build and maintain a risk register to track potential issues and meet SOC 2’s risk assessment requirements. Regularly update the registry to reflect new threats and business changes.
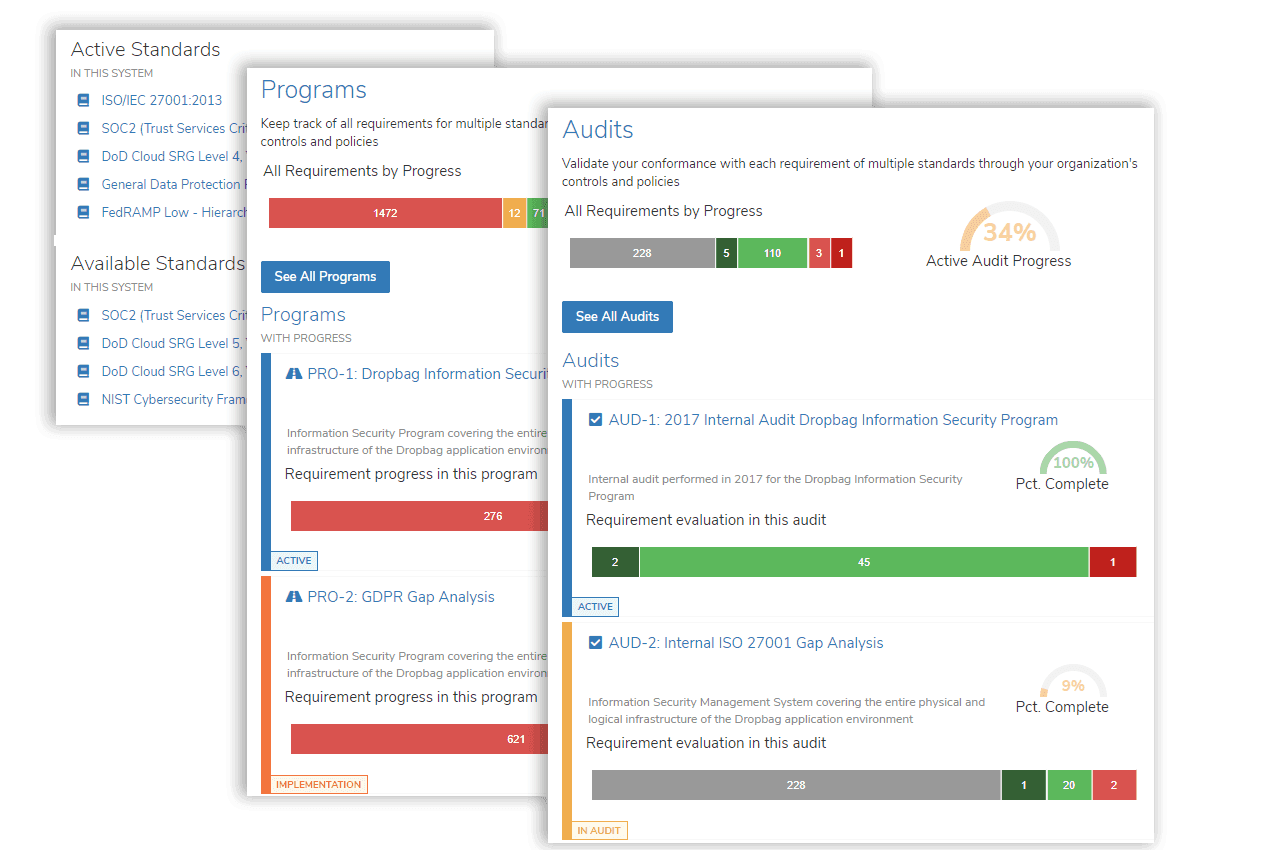
Dashboards and Reporting
Access at-a-glance dashboards for full visibility into your compliance program. Generate executive summaries or detailed audit-ready reports to meet the needs of different stakeholders.
Maintaining Continuous SOC 2 Compliance
SOC 2 compliance isn’t a one-and-done task. It’s an ongoing process that requires vigilance, consistency, and a proactive approach. To remain compliant throughout the year, organizations should build SOC 2 requirements into their day-to-day operations.
A few best practices to help keep your SOC 2 status in good standing include:
Regularly Review and Update Controls: Schedule periodic reviews of your controls to ensure they’re still aligned with current frameworks and business practices. Make updates as necessary when your processes, technology, or team structure changes.
Continuous Employee Training: Foster a culture of security by delivering ongoing security awareness and role-specific training. Equip every team member to recognize threats and follow protocols that support compliance.
Keep Risk Management Front and Center: Refresh your risk register periodically to account for emerging threats or business changes. Regular risk assessments will help you catch potential gaps before they escalate.
Automate Evidence Collection: Use tools or systems that streamline evidence gathering so you can easily demonstrate compliance whenever required, not just during the annual audit cycle.
Monitor and Respond to Incidents: Develop and maintain robust incident response procedures. Rapid detection, documentation, and response keep small issues from snowballing into larger problems—and ensure you stay compliant.
By weaving these practices into everyday workflows, organizations can reduce the stress of audit windows and maintain a high level of trust with their partners and clients year-round.
Key Takeaways
Systems and Organization Controls (SOC) are standards for measuring the effectiveness of an organization's financial information and data management practices.
There are multiple versions of SOC reports, including SOC 1, 2, and 3, and two sub-types of SOC 2, Type 1 and 2.
SOC 2 Type 1 reports detail the design and suitability of a company's controls, while Type 2 reports assess both the design and the operating effectiveness of the controls.
Type 1 is best suited for smaller companies with less sensitive data and less stringent security requirements. On the other hand, Type 2 is recommended for larger companies with sensitive data or operating in heavily regulated industries.
Achieving SOC 2 Type 2 compliance requires a thorough examination of a company's policies and controls over an extended period, usually 6 months to a year.
Type 2 demonstrates superior data security and control systems and allows companies to engage larger and more security-conscious organizations.
StandardFusion is a comprehensive GRC software for managing SOC compliance, offering features such as task management, control management, and reporting capabilities.
Regardless of which SOC report you need, StandardFusion is a fully featured GRC platform designed to simplify compliance for any framework. Our software helps you easily plan, execute, and keep up with regulatory requirements for an efficient and effective management experience.








