Published on: Apr 20, 2023
Network Security & GRC: Overcoming Business Vulnerabilities
In the current information security landscape, network security has become the backbone of any modern business, ensuring your digital assets stay protected against cyber threats.
This article will explore the ins and outs of network security, why it's vital for your business, how to manage vulnerabilities, and how Governance, Risk, and Compliance (GRC) can help strengthen your security.
Let's jump in!
What is Network Security and Why Should You Care?
Let's quickly define what we are talking about. Network security is a set of measures and technologies designed to protect computer networks from unauthorized access, misuse, modification, or destruction.
It includes some of the following tools and practices:
Firewalls
Intrusion detection and prevention systems
Antivirus software
Encryption
Networking security is vital for your business, but why?
Well, organizations depend on their networks for communication, collaboration, and data storage. However, the same networks can also be vulnerable to a range of security threats.
There are many reasons for you to take network security seriously, the most significant being protecting sensitive information.
In today's digital age, businesses and individuals store tons of personal and confidential data online, making it a great target for cybercriminals.
Unfortunately, a breach in your network security can lead to a range of consequences, such as:
Financial loss
Legal repercussions
Damage to a company's reputation
Loss of customer trust and more
Wait, that's not everything. There's one more big challenge.
Network security threats continue to evolve rapidly due to new techniques and vulnerabilities emerging daily. This means you must constantly maintain security measures to protect your networks from potential threats.
The Value of a Security-Conscious Culture in Risk Management
While robust policies and cutting-edge tools are critical, the human element remains one of the most influential factors in effective risk management. Building a security-conscious culture—where every team member understands their role in protecting sensitive information—can amplify your ability to manage risk across the organization.
Why does this matter? Every employee, from entry-level staff to executive leadership, makes decisions that can either strengthen or inadvertently weaken your security posture. Not every decision will trigger alarm bells, but something as innocuous as sharing company details on social media or responding to an unusual email can open new avenues for cyber threats like phishing and social engineering.
Take, for example, the common practice of publicizing staff profiles on platforms like LinkedIn. While it’s great for networking, it can also provide cybercriminals with ammunition to craft convincing spear-phishing campaigns targeting your team. If employees recognize unusual patterns—such as unexpected webinar invitations or suspicious attachment requests—they’ll be more likely to alert IT right away if they’re trained to be vigilant.
Fostering this type of awareness doesn’t eliminate risk altogether, but it does empower your workforce to serve as an early warning system. The result? Security teams gain faster visibility into emerging threats, and your organization can react swiftly, sometimes stopping an attack before it gains traction.
Overview of Network Vulnerabilities
Network security vulnerabilities refer to weaknesses or flaws in the network infrastructure, devices, protocols, or applications. As a result, cybercriminals can exploit any of these to gain unauthorized access to sensitive information, disrupt network operations, or compromise data integrity.
The range of network vulnerabilities is extensive and constantly growing, making it challenging for organizations to keep up with the latest threats and vulnerabilities.
Despite the best efforts of IT teams, no network can be completely immune to security threats. There are many types of network security vulnerabilities, including:
Weak or easily guessable passwords
Unsecured or misconfigured network devices, such as routers and switches
Malware, including viruses, Trojans, and worms
Social engineering attacks, including phishing and spear-phishing
Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks
SQL injection attacks and other web application vulnerabilities
Unpatched or outdated software
Man-in-the-middle (MITM) attacks
Unauthorized access or privilege escalation
Physical security vulnerabilities, such as unsecured server rooms and data centers
Although the list could be much longer, this is enough for now. The key here is that understanding the network security vulnerabilities is an essential first step in creating an effective security strategy.
By identifying potential risks, you can develop a plan to protect your networks and data from malicious attacks.
What Is Penetration Testing and How Does It Help Discover New Vulnerabilities?
Now, let’s talk about one of the most powerful tools in your security toolbox: penetration testing (also known as “pen testing” if you’re feeling cool and techy).
At its core, penetration testing is the process of simulating real-world cyberattacks against your network, systems, apps, and even your own people—before the bad guys try their luck. The idea here is simple: you invite skilled security professionals (sometimes called ethical hackers) to try and break into your environment just like an actual attacker would.
So why bother with pen testing when you already have firewalls and antivirus humming quietly in the background? Because while automated tools catch common weaknesses, penetration testing digs deeper to find the kinds of vulnerabilities that often slip through the cracks. Think unknown bugs (zero-day exploits), subtle misconfigurations, and clever tricks that only a human attacker would spot.
Here’s how penetration testing helps you:
Identifies Hidden Weaknesses: Sometimes vulnerabilities aren’t on any public list. Pen testing reveals them by actively poking and prodding your systems in creative ways.
Shows Real-World Risk: These tests demonstrate how an intruder could move through your network, what data they might access, and how much havoc they could cause. You get a clear picture of your true exposure—not just theoretical threats.
Guides Security Improvements: You’ll get a report with prioritized action items: what was found, how it was exploited, and what you should fix first. This helps you close gaps before attackers can exploit them.
Not all penetration tests are created equal. Depending on your unique needs, you might consider:
External penetration testing: Tests how your internet-facing assets—like websites, email servers, or cloud resources—stand up against attacks from the outside world.
Internal penetration testing: Simulates what could happen if an attacker gets inside your network, whether from a compromised device or a rogue employee, and tries to move laterally to reach sensitive data.
Social engineering tests: Evaluates how employees respond to phishing emails, phone scams, or even physical attempts to breach security. It’s a great way to test the human element.
Web application testing: Focuses specifically on your web-based applications, hunting for vulnerabilities like SQL injection, cross-site scripting, and more.
By regularly investing in penetration testing, you ensure that your security defenses aren’t just theoretical—they’re battle-tested. It’s a bit like hiring someone to proofread your defenses before the hackers do.
Types of Penetration Testing
Now that we've laid the groundwork on vulnerabilities, you might be wondering: how do you actually discover these weaknesses before the bad guys do? Enter penetration testing—sometimes called "pen testing"—which is like hiring ethical hackers to test your digital fortress.
But not all penetration tests are created equal. There are several flavors, each targeting a different area of risk:
External Network Testing
This is the classic test most people imagine: experts attempt to breach your systems from the outside, just as a cybercriminal would. The focus here is on your public-facing infrastructure—think websites, email servers, and other services accessible from the internet. It's a great way to see how exposed you are to the wider world.Internal Network Testing
Here, the scenario changes: what if someone already has access to your internal company network, whether that’s from a rogue employee or a hacker who slipped past your first line of defense? These tests show how an attacker could move around inside your systems, escalating their privileges or accessing sensitive data.Social Engineering Testing
Technology isn’t the only vulnerability—sometimes, the weakest link is human. Social engineering tests simulate phishing emails, phone calls, or even unauthorized visitors, putting your team's security awareness to the test. Can your staff spot a fake request for a password reset or an email that just looks… off?Web Application Testing
As businesses move ever more functions online, web applications become ripe targets. This type of testing digs deep into your website and apps, hunting for flaws like SQL injection (remember the infamous Target breach?), cross-site scripting, and other ways attackers might siphon off valuable data.
By using a combination of these penetration testing types, businesses like yours can gain a clearer picture of where risks lurk and where improvements are most urgently needed.
Simulating Attack Scenarios for Better Risk Management
One practical way organizations can strengthen their risk management strategies is by running simulated attack scenarios within their network environment. These simulations, often referred to as "red team" exercises or penetration testing, allow you to proactively uncover weaknesses by mimicking real-world cyberattacks.
Here’s how this works:
Mapping critical business applications: First, identify and chart how your essential applications interact within your network. This provides clarity on where sensitive data flows and which systems are most crucial to protect.
Conducting "what-if" scenario testing: By simulating different attack paths—such as unauthorized access attempts, malware outbreaks, or privilege escalation—you can see how your defenses would respond. These exercises reveal potential gaps in your security posture that may not be obvious during routine checks.
Analyzing response and remediation: After running these test scenarios, evaluate how quickly and effectively your team can detect, contain, and remediate threats. Use these insights to refine your policies and procedures, ensuring you’re ready for the unexpected.
By regularly performing controlled attack simulations, organizations can gain a deeper understanding of their security strengths and weaknesses, helping to inform a more robust and resilient risk management plan.
Why False Positives Matter in Risk Assessment
One key aspect you shouldn't overlook when managing network security is the impact of false positives during risk assessments. A false positive occurs when a security tool mistakenly identifies harmless activity or a non-existent vulnerability as a threat. While this might sound like a minor annoyance, these mistakes can have several unintended consequences.
The most direct issue? False positives distort your view of your network's real risk landscape. When your systems flag events or vulnerabilities that aren't truly threats, you might end up diverting time, attention, and budget towards solving problems that don't actually exist. For example, deploying extra security controls or responding to flagged incidents can take resources away from genuine vulnerabilities—potentially leaving your organization exposed where it matters most.
There’s also an operational risk. Relying on automated systems like XDR solutions or SOAR platforms, it’s not uncommon for legitimate business activity—such as an executive dialing in from an international conference—to be interrupted because it’s misclassified as suspicious. Blocking critical communications or access due to a false alarm could hinder daily operations and even impact business continuity.
In short, being vigilant about false positives helps ensure your risk management efforts stay focused and your defenses are truly aligned to actual threats—not just noise. By refining your risk assessment processes to distinguish between real risks and false alarms, you improve both your efficiency and your organization’s overall security posture.
What Is a Risk Register and How Does It Support Risk Management?
To build an effective network security strategy, you need more than just technical controls. You also need a structured approach to identifying and documenting risks. This is where a risk register comes into play.
A risk register is essentially a centralized document or tool that helps organizations systematically list and track potential risks, especially those that could impact projects, operations, or your overall security posture. Instead of leaving risk awareness to chance, the risk register brings clarity and organization to the process.
Here’s how it typically works:
Risk identification: List potential risks in plain language with a short description, so anyone on your team can quickly grasp what’s at stake.
Classification: Assign a category (e.g., operational, compliance, technical) to clarify where the risk falls and what part of your organization it may affect.
Assessment: Estimate the likelihood (how probable is it?) and the potential impact (how severe would the consequences be?) of each risk.
Mitigation planning: Outline how you’ll respond if the risk materializes—think of this as your backup plan.
Prioritization: Rank the risks, helping your team focus resources on what’s most urgent or dangerous.
Risk registers aren’t just “set and forget” documents. In practice, they’re living tools, updated as new risks emerge or as existing risks evolve. Project managers often use them from the very beginning of a new initiative, but they’re just as valuable for ongoing operational activities.
Most importantly, by maintaining a risk register, you gain visibility into common patterns or recurring issues. If you see that certain types of risks appear across multiple registers or departments, this signals a broader area of concern requiring attention.
A well-maintained risk register enables more informed decision-making, helps you prioritize mitigation efforts, and supports compliance—not only with internal security policies but also with regulatory requirements. Ultimately, it’s a cornerstone for managing uncertainty, reducing disruption, and enhancing your organization’s resilience.
What Information Should Be Included in a Risk Register?
A well-constructed risk register is the backbone of effective risk management and an essential part of your GRC toolkit. But what exactly needs to go into it? Here are the key components you should include:
Risk Description: Clearly state what the risk is—short, sweet, and to the point.
Risk Category: Specify which part of your organization, asset, or process the risk could impact, whether that's infrastructure, personnel, or data security.
Likelihood: Estimate how probable it is that this risk will materialize. Use qualitative scales (like low/medium/high) or quantitative percentages, depending on your organization's preference.
Potential Impact: Outline what could happen if the risk becomes reality. Think about financial loss, reputational damage, operational disruption, or regulatory consequences.
Mitigation Measures: Detail the preventative and responsive actions in place or proposed to reduce the likelihood or impact of the risk.
Priority or Risk Score: Rank or rate the risk to help you and your team focus resources where they're needed most. This can be based on a combination of likelihood and impact.
By documenting these elements for each identified risk, you make it far easier to track, prioritize, and tackle vulnerabilities head-on, ensuring nothing slips through the cracks as your environment evolves.
Identifying and Consolidating Risk Registers Across Projects
Managing network security isn't just about knowing what risks exist—it's about understanding where those risks live throughout every corner of your organization. One practical step in this process is to identify and consolidate all the risk registers maintained across various projects, departments, and teams.
So, how does an organization do this efficiently? Here's a streamlined approach:
Start with Project Managers and Team Leads: Touch base with project owners across the company. Most established projects—especially larger, ongoing ones—should already have risk registers in place. These documents typically outline key risks, their likelihood and potential impact, and current mitigation strategies.
Conduct a Discovery Process: Not all initiatives will have formal documentation. For smaller projects or new efforts, initiate a review with team leads to surface ad-hoc or undocumented risk lists. Encourage teams to create simple risk registers if none exist.
Standardize Risk Information: As you gather registers, you'll likely notice variations in how risks are categorized and described. Create a uniform template (including fields like description, likelihood, impact, mitigation plan, and priority) to ensure consistency across the organization. This makes it easier to compare and consolidate risks from multiple sources.
Centralize the Data: Use a central repository—whether that's a shared drive, a project management tool like Jira, or a dedicated GRC platform—to store all risk registers. This shared space should be easily accessible to key stakeholders for ongoing updates.
Analyze for Patterns and Overlaps: Once consolidated, review the data for recurring risks and common problem areas. Identifying patterns can reveal systemic weaknesses, highlight the need for organization-wide policies, and guide targeted mitigation efforts.
Regularly reviewing and updating this consolidated view ensures everyone—from IT to compliance to executive leadership—has a comprehensive understanding of current risks and mitigation strategies. By proactively seeking out and unifying these registers, you not only reduce redundant work, but also gain valuable insight into your organization's threat landscape.
The Importance of GRC in Network Security
As you saw in the previous section, network security vulnerabilities are numerous and constantly evolving, making it challenging for organizations to manage and mitigate them effectively.
This is where Governance, Risk, and Compliance (GRC) comes in.
GRC provides a comprehensive and integrated approach to managing risk, which includes assessing, monitoring, and mitigating risks across the organization.
In the context of network security, GRC can help you identify and manage the risks associated with your IT systems and infrastructure. We'll give you some examples shortly.
What are the challenges of managing and mitigating network security vulnerabilities?
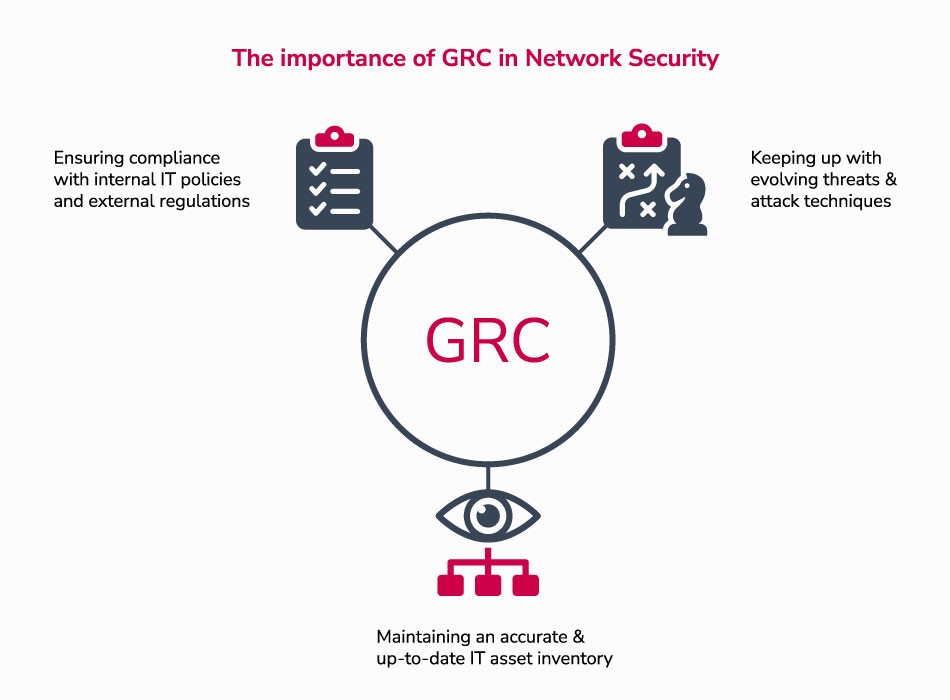
Some of the critical challenges that GRC can help with include the following:
Ensuring compliance with internal IT policies and external regulations
Keeping up with constantly evolving threats and attack techniques
Maintaining an accurate and up-to-date IT asset inventory
Let's briefly explain these.
First, ensuring compliance with internal IT policies and external regulations is critical to maintaining a solid security posture. It would be best if you had clear policies and procedures in place to ensure that your IT systems and infrastructure are secure and in compliance with applicable regulations and industry standards.
Second, keeping up with evolving threats is vital to managing network security vulnerabilities, The reason? Cybercriminals are continually developing new attack techniques, and you need to be able to adapt and respond quickly to these threats.
Finally, maintaining an accurate and up-to-date IT asset inventory is essential for effective vulnerability management.
You need to know what IT assets you have, where they are located, and how they are configured in order to identify and remediate vulnerabilities.
How GRC Helps Address Network Security Challenges and Simplifies Compliance
A GRC program can help you design and implement policies and procedures, assess and monitor risks, and ensure compliance with internal and external regulations and industry standards.
Specifically, GRC allows you to keep up with regulatory changes by providing regular updates and risk assessments. It can also assist with automating compliance tasks, such as monitoring network activity and generating compliance reports.
Governance, Risk, and Compliance is vital to stay updated with the latest security threats by providing real-time alerts, threat intelligence, and automated response capabilities. It can help you identify potential vulnerabilities and prevent attacks before they occur.
Finally, a robust GRC program can help you manage your IT assets by providing comprehensive asset management capabilities. This includes tracking the location, status, and configuration of each asset, as well as monitoring changes to the asset inventory in real-time.
Overall, these are some of the benefits of using a GRC program for network security:
Improved visibility into IT risks and vulnerabilities
Increased efficiency and effectiveness of risk management processes
Improved compliance with internal and external regulations and industry standards
Enhanced collaboration and communication across the organization
Improved decision-making and risk prioritization based on data and analytics
The bottom line?
GRC helps you take a more proactive and holistic approach to managing your network security risks and improving your company's security posture.
StandardFusion: An Empowering GRC Tool to Secure Your Network
Maintaining the security of a network is a complex and ongoing responsibility. Cybercriminals can exploit numerous vulnerabilities, from weak passwords to unpatched software and physical security weaknesses.
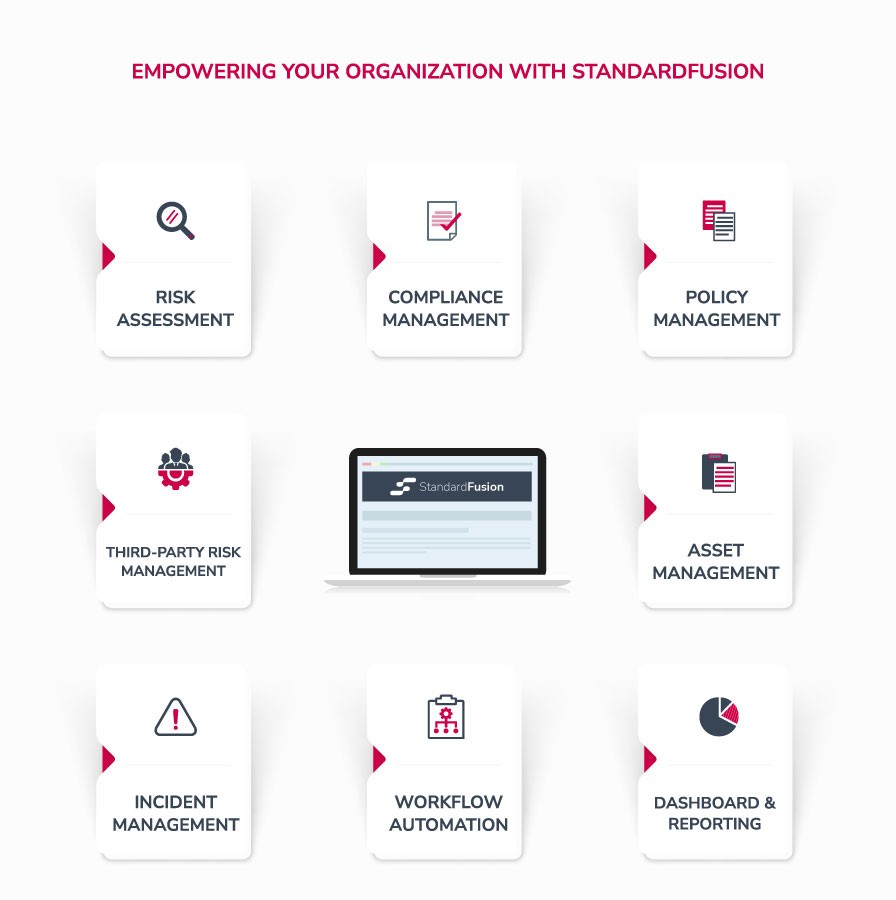
StandardFusion can help you address these vulnerabilities and maintain a secure network environment with the following features:
Risk Assessment
StandardFusion's GRC software enables you to identify, evaluate and prioritize risks to their network security. By analyzing the risk associated with different assets, processes, and systems, you can prioritize their remediation efforts and allocate resources more effectively.
Using our GRC tool, you can address vulnerabilities such as unpatched or outdated software, unsecured or misconfigured network devices, and weak or easily guessable passwords.
Compliance Management
StandardFusion helps you keep track of regulatory requirements and industry standards. It provides a centralized repository for policies, procedures, and controls.
In short: All your compliance management needs are bundled into an easy-to-use interface for managing a new implementation or existing GRC program.
With a robust compliance management tool, you can overcome vulnerabilities such as social engineering attacks, unauthorized access, and privilege escalation.
Policy Management
Effective policy management is crucial to preventing network security incidents. StandardFusion's policy management enables you to create and manage IT policies and ensures they are consistent with industry best practices and regulatory requirements.
Doing this correctly will help you prevent network security incidents by ensuring everyone in the organization follows the same guidelines and protocols.
Policy management can reduce vulnerabilities such as man-in-the-middle (MITM) attacks and physical security vulnerabilities.
Third-Party Risk Management
Our Third-Party Risk Management tool helps you assess the security risks associated with vendors and suppliers. It enables you to evaluate third parties based on their security controls, compliance with regulations, and past security incidents.
With this information, you can identify high-risk vendors and take action to mitigate the risks they can introduce to your organization.
In addition, Third-Party Risk Management enables you to track vendor compliance with security policies and requirements. You can set up automated assessments to ensure that vendors meet their contractual obligations and notify them when they are not compliant.
Asset Management
StandardFusion's asset management enables you to maintain an accurate and up-to-date inventory of your IT assets and provides visibility into their security status. This helps you identify and mitigate vulnerabilities such as malware, viruses, Trojans, and worms.
Incident Management
In the event of a security breach, StandardFusion's incident management helps you respond quickly and efficiently to incidents. It ensures that you take the appropriate measures to contain and mitigate their impact.
Workflow Automation
By automating critical processes, StandardFusion's workflow automation feature reduces the workload on IT staff and improves efficiency. This feature can address vulnerabilities like SQL injection attacks and other web application vulnerabilities.
Dashboard and Reporting
StandardFusion's dashboard and reporting feature provides real-time visibility into critical risk and compliance metrics, enabling you to identify areas of concern and take corrective action quickly.
But wait — there's more.
We've covered why vulnerability management is critical to your cybersecurity program and how it should be part of your overall GRC program. To make this connection seamless, you can import Qualys vulnerabilities and other relevant security data spreadsheets into StandardFusion, making it easier to track and manage them, all while allowing you to take advantage of our powerful features.

Connect with our team to see how to use it in your GRC program.
Seven Best Practices for Effective Risk Management in Network Security
So, what does effective risk management in network security actually look like in practice? Here are the top seven strategies every organization should have in their toolkit:
Build a Security-First Culture: Encourage everyone—not just your IT team—to view security as their responsibility. Regular training sessions, clear policies, and open communication about risks go a long way in making security awareness part of your organization’s DNA.
Document Risks Thoroughly: Use a risk register or similar tracking tool to log details about potential risks. Documenting the “what, where, and how bad” of each vulnerability helps you keep a clear picture of your network’s weak spots and prioritize your response.
Emphasize Proactive Solutions: Don’t wait to respond until threats materialize. Whenever possible, remediate vulnerabilities with preventative, low-cost fixes. Quick wins—like updating passwords or patching software—can make a big difference.
Treat Risk Management as a Journey: Risk isn’t static, so managing it shouldn’t be either. Set up regular reviews and updates to your risk management processes to stay one step ahead of emerging threats.
Prioritize Regular Penetration Testing: Bring in white-hat hackers or run authorized penetration tests to uncover unknown vulnerabilities before cybercriminals do. Engaging with frameworks like those from OWASP can help you stay up to date on testing best practices.
Set Clear Benchmarks for Risk Tolerance: Use established frameworks, such as the NIST Cybersecurity Framework, to help define your level of acceptable risk. This makes it easier to make balanced decisions about where to invest time and resources.
Account for False Positives: Not every alert signals a real threat. Regularly review and fine-tune your detection systems to minimize false alarms, so your team spends time on what truly matters.
Mastering these best practices can help make your network security strategy more resilient, more responsive, and—most importantly, more effective at keeping threats at bay.
Key Takeaways
Network security is crucial for protecting sensitive data and preventing unauthorized system access.
Network security vulnerabilities are numerous and constantly evolving, making it challenging to manage and mitigate risks.
Governance, Risk, and Compliance (GRC) programs help manage network security risks by ensuring compliance with internal policies and external regulations, keeping up with evolving threats, and maintaining an accurate IT asset inventory.
GRC tools like StandardFusion offer a range of features to manage network security risks, such as policy management, risk assessment, vendor management, incident mangement, and reporting.
Policy management can help with network security by ensuring that IT policies and procedures are up-to-date and consistently applied across the organization.
Other key features of GRC software for network security include centralized documentation and data management, automated workflows, real-time monitoring, and analytics.
Implementing a GRC program for network security can simplify compliance, improve risk management, and enhance overall security posture.
Explore the benefits of a GRC software solution tailored to your organization's needs, offering automation capabilities and alignment with your business objectives.
Connect with our team and discover the advantages of network security management software in elevating efficiency and achieving your organizational goals.







