Published on: May 26, 2022
The Vendor Risk Management Lifecycle: Aligning Your Business' and Third Parties' Goals
This is the final part of the vendor risk management (VRM) series. The Vendor Risk Management lifecycle!
In this one, we will cover the various stages of the vendor risk management lifecycle and provide some useful tips for each phase to optimize the program and protect the confidentiality and integrity of your organization.
Let's jump right into it!
Vendor Risk Management Lifecycle: The Foundations
When we think about the vendor risk management lifecycle, the simplest way to visualize the phases is to compare it to a concept we are quite familiar with building, managing, and ending relationships. Whether they are relationships of a personal or professional nature, our interactions will typically move through the following stages:
Stage 1: The discovery phase when we are learning about the other party.
Stage 2: The relationship phase when the connection begins to grow and develop.
Stage 3: The termination phase when one of the parties no longer wants to continue the partnership (note: this phase may not materialize if both parties are fully invested in keeping the relationship going).
Now that we've recapped the stages of the vendor risk management lifecycle, let's take a deeper dive into the phases that each organization will encounter throughout its vendor risk management process.
While procedures can vary across industries and organizations, a solid understanding of the basic framework will enable you to protect your organization from unmitigated vendor risk. As we navigate through each phase, useful tips will be provided to guide you along the journey.
Managing the Vendor Risk Lifecycle
Stage 1: The Discovery Phase
At the start of the discovery phase, the organization has identified a business need that can be achieved via procuring goods or outsourced services. After building the business case and obtaining approval, the work begins on sourcing and vetting prospective vendors. Key steps during this phase include:
Document evaluation criteria;
Vendor identification, evaluation, and selection;
Due diligence and contract management.
Document Evaluation Criteria
Being prepared in advance is key. Before initiating discussions with vendors, document your requirements on paper. This includes identifying your key objectives and quantifying evaluation criteria in a vendor assessment checklist. Start by capturing your preliminary thoughts about:
The business needs and objectives (the "why").
The operational requirements between "must-have" vs. "nice to have" (the "what").
Estimated implementation goals and budget limits (the "how" and "when").
The level of importance of each requirement (the "what").
Using a checklist format would be the most pragmatic and practical. This format will enable you to efficiently track the vendor's responses during the evaluation process and quickly change the structure and content as the evaluation progresses.
Illustrative Template:
A sample of a vendor assessment checklist may look something like this:
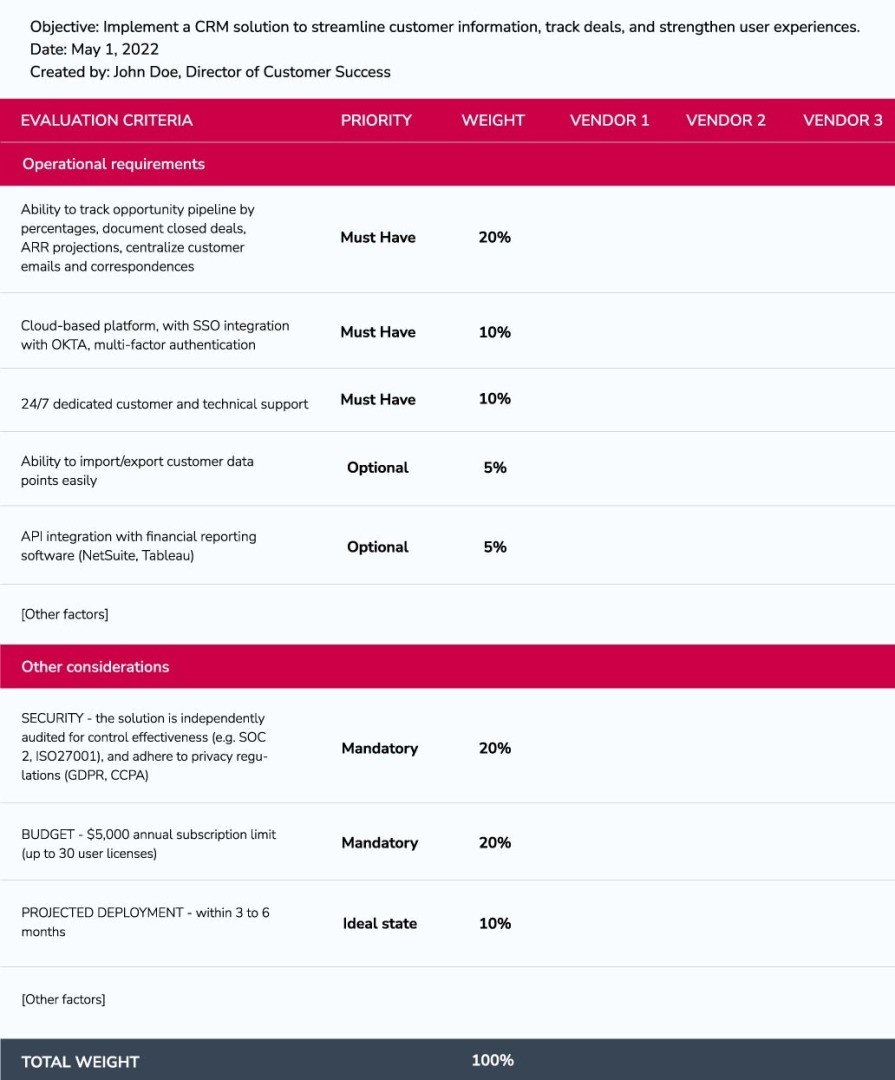
Shortlist Your Selection to Two to Three Vendors
To balance effectiveness and resource availability, it's best practice to shortlist between two to three vendors for comparative purposes. Even though it seems tempting to compile a massive list of vendors to assess, the cost/benefit ratio to perform a deeper analysis of each vendor is not always feasible.
If you are faced with the challenge of reducing your list to a manageable limit, reach out to existing business partners and associates for further guidance and suggestions.
Unless you are strongly inclined to consider only one specific vendor because the vendor is an industry leader or operates in a market with minimal competition, having several vendors to choose from is beneficial because it:
Provides greater diversity and options for consideration (not putting all your eggs in one basket).
Offers insights on additional features or services that were not identified when the business case was initially designed.
Optimizes your likelihood of obtaining better contractual terms, pricing, and services.
Vendor Evaluation and Selection
Creating a consistent method to evaluate vendors is vital. It will ensure that every single vendor is graded similarly and that no significant aspects will be overlooked. Some organizations may vary in approach during this step " from executing a structured RFI/RFP process to more casual vendor discovery calls. Regardless of the methodology selected, you must leverage the vendor assessment checklist previously created as guidance when discussing your business needs with prospective vendors.
It will be beneficial to supplement the vendor responses with a demo of the software, request for temporary access to a sandbox environment to assess the functionality, or review pertinent artifacts to confirm the vendor's adherence to financial, regulatory, or compliance requirements. For service-based offerings, an organization should also consider asking for references to validate the quality of the vendor services.
Due Diligence and Contract Management
After choosing a vendor, the final stage would be to complete the due diligence reviews and solidify the arrangements in a contract.
Depending on the nature of the services to be provided, the organization should review these foundational documents as part of their due diligence (as applicable and relevant):
Company information: Legal name, head office address, ownership structure, tax numbers, business license, incorporation documentation.
Ratings: Dun & Bradstreet report, credit report, BBB check.
Government checks: OFAC/PEP checks, security clearances.
Financial and security checks: Financial reports, SOC report, trust center artifacts, certificate of insurance.
Having a good handle on your contracts will save time and money. Well-defined and executed contracts are the best protection against unexpected headaches and problems in the future. Ideally, you should have standard vendor templates that will help streamline negotiations and set expectations to protect your organization from various aspects of vendor risk.
How to do it?
Start with either yours or the vendor's templates to initiate negotiations. At a minimum, the standard set of agreements should include the following:
Service Level Agreement: Defines the terms and conditions, including the scope of work or goods to be provided, timing of services, payment terms, responsibilities, renewal and termination, indemnification, right to audit, and enforcement clauses.
Mutual Non-Disclosure / Confidentiality Agreement: A binding contract between two or more parties that prevents the disclosure of sensitive corporate information from being shared with unauthorized parties.
Acceptable Use / Security Addendum: Outlines the rules and obligations of the vendor to protect the organization from inappropriate use of assets, safeguards to reduce the risk of cyber-attacks, and hold the vendor accountable for maintaining compliance with regulations and standards.
There are plenty of online examples that organizations can leverage to design their own. Depending on the nature of your business and the industry in which the organization operates, it would be prudent in some cases to engage external legal counsel and technical expertise to design regulatory or compliance clauses. With evolving cybersecurity and privacy mandates, online templates may be insufficient or not updated to reflect compliance with current laws and regulations.
After the parties successfully sign the contracts, it's equally important to keep them organized and centralized in a contract repository. This will support subsequent administrative tasks such as contract tracking, reviews, renewals, and updates.
Stage 2: The Relationship Phase
Once the vendor starts providing goods or services, monitoring vendor performance is critical. It's essential to remain vigilant of any new risks that may surface over time and closely watch vendors to ensure they perform as expected. Ongoing activities would include implementing protocols to:
Monitor vendor service and performance delivery (SLA tracking).
Validate ongoing vendor compliance with regulatory or cybersecurity obligations, including changes to these obligations (periodic assessments).
Address any service, regulatory, or cybersecurity gaps promptly (SLA remediation).
You want to position the organization to be well-informed and be able to react quickly in the event of supply chain disruptions or new vendor risk exposures. The previous is even more vital if changes with the vendors will negatively impact the SLA deliverables and your organization's regulatory or cybersecurity obligations.
To accomplish a repeatable and scalable cadence for continuous monitoring activities, we suggest the following best practices:

Stage 3: The Termination Phase
There comes a time when either the organization, vendor, or both parties are ready to end the business relationship. This scenario may arise due to various factors, including vendor performance history, price considerations, or the organization that has outgrown the services provided by the vendor.
Depending on the role of the particular vendor in your supply chain, the offboarding may be pretty straightforward with minimal business disruptions. The organization should deploy its exit strategy for business-critical vendors with greater complexity to ensure the end of the relationship follows contractual terms and conditions.
A vendor termination checklist may include the following workflows:
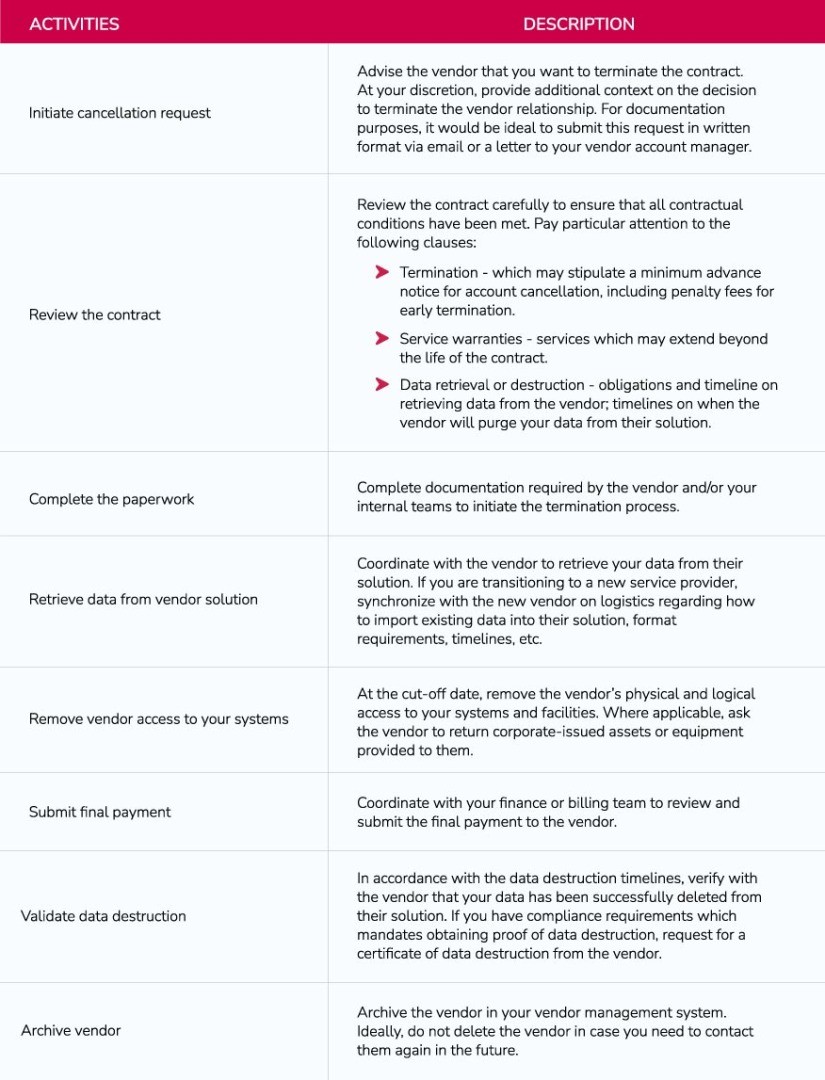
Accountability - Whom to Involve Internally
Finally, in order to mobilize these valuable tips into action, we must recognize the topic of accountability and who will take the lead on the various activities. Depending on the size of your organization, the tasks may require support from multiple departments.
As a reference point, key stakeholders generally include the following teams:
Asset owner: Beneficiary teams and users of the solution.
Finance: Sourcing and procurement.
Legal: Contract negotiations.
Information Security, Compliance, Privacy: Matters related to cybersecurity, compliance, privacy, and data governance.
IT and Operations: Provide support to implement, manage, and deactivate the services.
The Vendor Risk Management Lifecycle
The vendor risk management lifecycle requires your organization to adopt the proper frameworks and regulations to ensure your business is safe while working with third parties.
In simple words, it helps you put the appropriate processes, systems, and policies in place to assess your vendors, track their performance and align your business and third parties' goals from discovery to relationship to termination phase.
Do you trust your vendor? Do you trust your third parties enough that you know they won't put you at risk? Vendor risk management will help you review areas of potential exposure and mitigate them before causing any severe damage to your organization.
Key Takeaways
In this article, we discussed the three stages of the vendor risk management lifecycle, which you can see as building, managing, and ending relationships.
The first stage is the discovery phase, during which the organization identifies a business need that can be fulfilled through procuring goods or outsourced services.
Critical steps in the discovery phase include documenting evaluation criteria, shortlisting vendors, and evaluating and selecting vendors.
The second stage, the relationship phase, is when the connection between the organization and the vendor begins to develop.
In the second stage, it's vital to monitor vendor performance. You should stay aware of any new risks that may arise and keep a close eye on the vendors to ensure they meet the expected performance standards.
The third stage is the termination phase, which may occur if one of the parties decides to end the partnership.
Eventually, the business relationship between an organization and a vendor may end. This can be due to a range of factors, such as the vendor's performance history, price considerations, or the organization's outgrowing of the services provided by the vendor.
You can manage vendors either manually or by leveraging technological advancements, such as using a GRC or VRM solution, to streamline workflows and enhance operational efficiencies.
Book a demo with our team to discover how you can transform your VRM lifecycle into a program that enables smarter vendor risk management decisions built on meaningful risk-intelligent analyses and proven results.
Optimize your potential to execute informed actions faster, better, and smarter.







