Published on: Nov 29, 2022
GRC and Cybersecurity: An Integrated Approach For Your Organization
When dealing with cybersecurity, GRC is frequently considered the least exciting part of business security. However, Governance, Risk, and Compliance can't be ignored, and this article will explain why.
Let's get started!
How GRC and Cybersecurity Work Together
While cybersecurity aims to protect systems, networks, devices, and data, GRC is the tool that will help your entire organization understand and communicate how to do it.
What does it mean?
GRC tools like StandardFusion can help you specify and implement the best practices and governance to ensure everyone is aware of the risks associated with their actions. Moreover, how these actions can affect your business security, compliance, and overall success.
In simple terms, GRC is the medium for creating awareness about cybersecurity's best practices to minimize risks and achieve business goals.
Why Should You Care About Cybersecurity
Cybersecurity helps you protect sensitive company data, personal and health information, intellectual property, and other systems from cyber-attacks and threats. However, this task has become increasingly challenging over the past few years.
Why is that?
Well, these are some of the main reasons:
The ever-increasing global connectivity
New hybrid work models
The popularization of cloud services, and
The evolution of technology, among others
Although all of these are great for business, they introduce new risks and challenges.
Here's what happens:
Cybersecurity has always been a crucial part of organizations. However, in today's interconnected landscape, your organization can't live without it " at least in the long term.

The Principles of GRC
Governance, Risk, and Compliance is a business strategy for driving a company's governance, enterprise risk management, and regulatory compliance.
From a cybersecurity perspective, GRC is a structured strategy to align IT with your business goals while effectively managing risks and meeting regulatory needs.
But let’s break it down further.
Governance refers to the framework of policies, procedures, and processes that dictate how an organization is directed and controlled. In the context of cybersecurity, governance ensures there are clear guidelines and responsibilities for safeguarding information assets. Effective governance doesn’t just keep things running smoothly—it creates an environment where employees feel empowered, and where behaviors and resources are well-coordinated to protect the business.
In this matter, you must follow the best practices and procedures to achieve business objectives and maximize your company's bottom line.
This is why GRC exists...
To mitigate any risk to productivity and your company's value by developing standards, policies, and regulations.
In addition to this, GRC helps you increase trust in your organization. This elevation in credibility comes from improved efficiencies, communication, employees' confidence to share information, and enhanced business results.
That's not all.
GRC provides companies with the tools to create a culture of value, where everyone is educated and empowered to make decisions that protect the company's value and reputation.
The Role of GRC in Cybersecurity
You need to align people, systems, and technologies with your business goals to have a reliable and effective cybersecurity program. This means everyone needs to understand and take the proper steps when performing their tasks—it's all about awareness and understanding.
Governance, Risk, and Compliance is the best tool to develop an integrated approach that focuses on accomplishing objectives while handling risks and acting with integrity.
Setting Clear Roles and Responsibilities
A critical aspect of GRC is ensuring that everyone knows exactly what their job is. It’s not just about general awareness; it’s about defining concrete roles for every stakeholder—whether that’s the board of directors, the CEO, the Chief Risk Officer, or the legal department. This clarity extends to the CIO, CTO, CFO, internal audit, finance, IT, and line-of-business managers. When each team understands their specific responsibilities, communication becomes more streamlined and accountability is baked into your cybersecurity strategy.
GRC is critical because it supports cybersecurity with vital business activities, such as:
Helping with the implementation of data manipulation procedures
Meeting industry and government regulations
Assigns functions and duties to business units and users, enhancing communication
Standardizing the best practices for teams to act with integrity and security
Unifies vocabulary across departments and teams
Supporting internal audits and encouraging continuous control monitoring
Assisting with risk mitigation internally and externally
By laying this foundation—where responsibilities are clear and communication is open—your organization is equipped not just to react to threats, but to proactively safeguard its value and reputation.
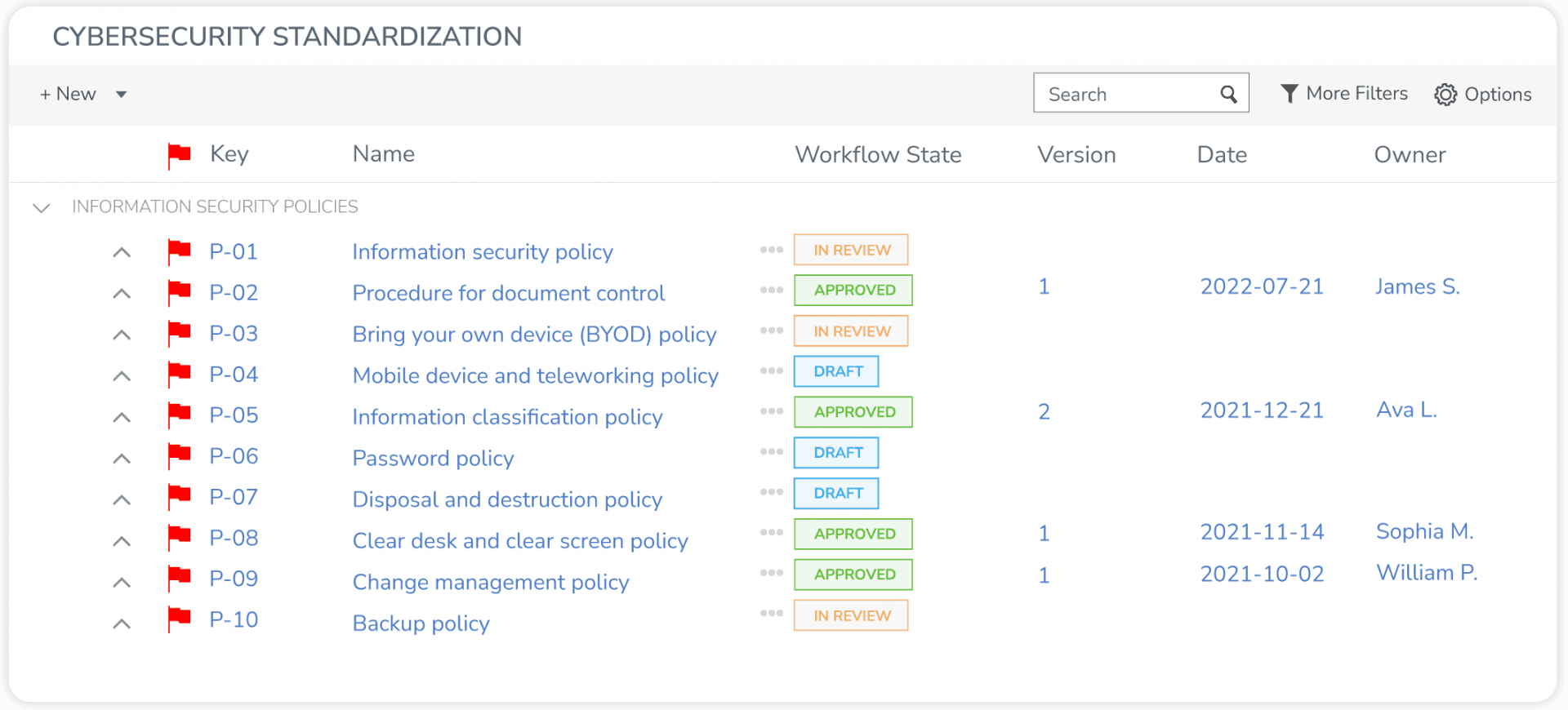
In addition, GRC provides you with a framework to integrate security and privacy with your company's overall objectives.
Why is this important?
Because it helps you to make informed decisions about data security issues quickly while still mitigating the risk of compromising privacy.
Navigating the Challenges of GRC Implementation
Of course, rolling out GRC practices across your organization isn’t always smooth sailing. There are a few hurdles businesses commonly encounter on this journey.
First up, you’ll often face some resistance to change—let’s be honest, not everyone leaps for joy when new policies hit their inbox. People get comfortable with their routines, and the shift toward standardized processes can ruffle feathers, especially when it affects multiple departments.
Another classic pitfall? The sheer complexity of weaving GRC frameworks like COBIT or ISO 27001 into your existing business fabric. Connecting different teams—HR, IT, finance, and more—so that everyone is on the same page takes more than just good intentions.
And as if that wasn’t enough, the regulatory landscape refuses to stay put. Rules and requirements from authorities like the GDPR, HIPAA, and PCI DSS are always evolving, which means your compliance targets can move at any moment.
So how do you overcome these roadblocks? It comes down to strong leadership at every level, open channels of communication, and a genuine commitment to ongoing improvement. When these elements are in place, integrating GRC into your cybersecurity program becomes much less daunting.
The Benefits GRC Offers Cybersecurity
The following are some of the essential benefits you need to aware of:
Third-party vendor selection: Organizations can use a third-party scorecard to collect basic details about vendors. This information may include: Financials, corporate reputation, network security, history of breaches, location, and more. A strong GRC model would support IT and security teams in selecting and vetting potential third-party vendors. Furthermore, GRC will support the creation of vendor assessments and mitigation strategies.
Risk mitigation: IT uses GRC to understand the scope of cybersecurity and record the strengths and limitations of the existing security program. Also, GRC allows organizations to outline and act on different threats, potential damages, mitigation strategies, and risk treatments.
Regulatory compliance: GRC is essential to regularly track compliance as new regulations evolve worldwide. Moreover, it helps your security teams be aware of changes quickly, providing time to plan and respond. GRC will help you produce and manage the policies, regulations, and standards to meet the constantly-updated business and industry regulations.
Data privacy: GRC enables you to stay on top of privacy regulations. But how? by allowing your IT team to ensure that the proper protection, logging, geographic storage, etc., are in place to safeguard customers' and employees' data.
Visibility: GRC's integrated approach allows you to gain visibility into every aspect of your security compliance programs. This is crucial as it enables different units, managers, and personnel to see the big picture. In addition, it helps you make data-driven and informed decisions.
In summary:
A well-planned GRC program enables you to:
Promote collaboration
Build a robust culture
Protect the company's value and reputation
Improves integration
Collect and keep high-quality information
Improve decision-making processes
Increase accountability
Increase efficiency and agility
Provide visibility
Reduces costs by supporting suitable investments
Why Do You Need an Integrated Approach?
Integrating GRC and cybersecurity is critical for your organization if you want to build a long-term, successful security strategy. Aside from speedy communication, balanced metrics, teamwork, and improved decision-making, the integration of GRC and cybersecurity gives you the following advantages.
First, an integrated approach minimizes manual input and the possibility of human error, decreasing costs and giving you more time to produce more value for your business.
Secondly, a powerful integration allows the board to clearly and comprehensively visualize the company's security posture. Therefore, by understanding the cross-functional posture, directors can elaborate better security stories to convey trust to customers and empower employees.
To sum up:
Cybersecurity and GRC work hand in hand towards a lower-risk future and value creation " they can't live without each other. While cybersecurity seeks to protect systems, networks, and data, GRC communicates the best approach to achieve so.
For instance, with an integrated approach, you will:
Enhance security posture
Set the tone for the entire company
Increase efficiencies
Tell better security stories
Improve visibility across the board
Get more support from the leadership
Avoid compliance/regulatory fines
Rolling Out and Testing a GRC Framework
Rolling out a GRC framework isn't a one-step affair—it's a purposeful process designed to keep your risk management and compliance efforts agile and effective as your environment evolves. Here’s how you can approach the process, building on the principles we’ve discussed so far:
1. Define Your Priorities and Objectives
Begin by outlining your primary risks and compliance obligations, such as regulatory requirements (think GDPR, SOX, HIPAA) or pressing data privacy challenges. Be clear about what success looks like so you can measure progress down the line.
2. Assess Current Capabilities and Identify Gaps
Examine your existing processes to uncover operational weaknesses. Are there unresolved issues—like third-party management blind spots or incomplete reporting—that need immediate attention? Identify where you need to shore up processes or controls.
3. Secure Commitment from Leadership
A sustainable GRC initiative thrives on strong support at the senior level. Engage your leadership team early to reinforce the importance of a risk-aware and compliant culture. Their backing is vital for both strategic direction and resource allocation.
4. Foster Organization-Wide Engagement
It’s not enough for leaders to buy in; employees at all levels should understand why GRC matters and how they fit into the program. Equip teams with the right knowledge, and promote a culture where accountability and collaboration go hand in hand.
5. Clarify Roles and Responsibilities
Explicitly define who owns each facet of GRC—from the board to line-of-business leaders, through to IT, audit, compliance, and legal. When everyone understands their part, accountability and efficiency skyrocket.
6. Leverage GRC Platforms for Execution
Use robust solutions, such as those aligned with frameworks from ISACA, NIST, or COSO, to streamline compliance tracking and risk management. The right tools bring consistency, reduce manual errors, and help you adapt procedures as requirements shift.
7. Pilot the Framework for Maximum Impact
Rather than launching organization-wide out of the gate, start with a pilot in select departments or functions. This controlled rollout lets you resolve issues, gather feedback, and demonstrate early wins—paving the way for a smoother implementation at scale.
By following these steps with a focus on communication, accountability, and continuous improvement, you set the stage for a GRC program that is resilient and forward-looking.
Empowering Cybersecurity Methodology
The OCEG has developed this Capability Model as an open-source methodology that combines the sub-disciplines of governance, risk, audit, compliance, ethics/culture, and IT into a cooperative approach.
However, you can manipulate this standard to address specific situations, from short projects to organization-wide rollouts. Some examples are:
Business continuity
Anti-corruption projects
Third-party management
Streamlining frameworks
The model is vital to articulating conversations about GRC capabilities with senior executives and managers. Also, you might use this GRC Capability Model with more specific functional frameworks, such as: ISO, COSO, ISACA, IIA, NIST, and others.
The GRC Capability Model enables your organization to document best practices to:
Standardize practices for things like policies and training
Unify vocabulary across disciplines
Define common information requirements
Define common components and elements
Identify communication for everyone involved.
But the benefits don’t stop there. When GRC practices are effectively implemented, organizations can experience:
Better Resource Management: Efficient GRC processes lead to optimized use of resources, reducing redundancies and improving productivity across teams.
A Culture of Continuous Improvement: Integrating GRC practices fosters an environment where ongoing enhancement and organizational resilience become the norm, not the exception.
Now, let's see how it works.
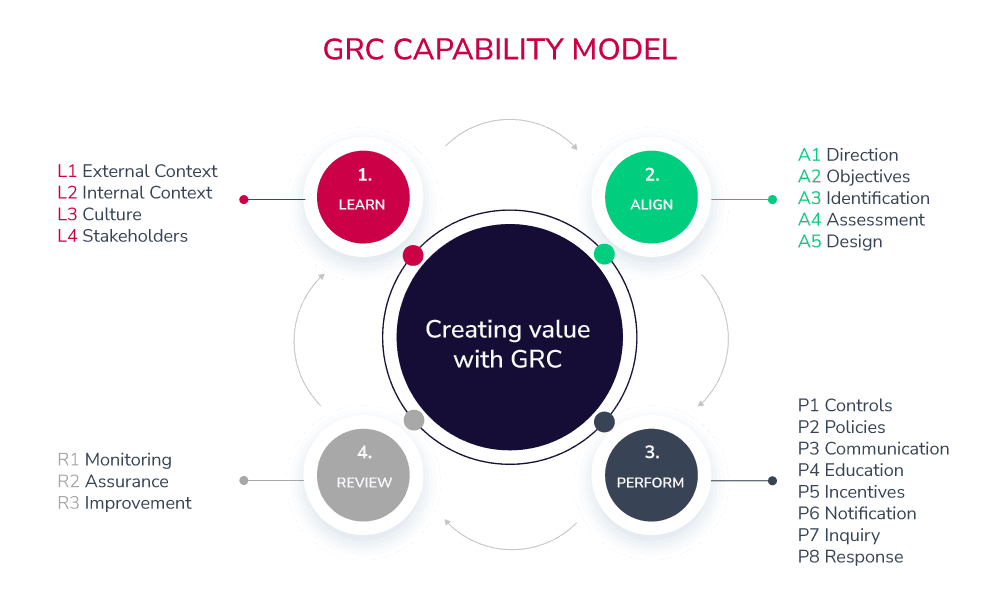
The Four Parts of the Capability Model
1. Learn
The central idea here is to identify your business culture, stakeholders, and organization's business procedures to successfully guide your goals, strategy, and objectives.
This is how it would look like:
Learning business plans and goals
Understanding strategic objectives
Being aware of the current and future compliance activities
Connecting with the key stakeholders
A strong start also means establishing clear goals—determining your greatest risks and challenges, from data privacy to government regulations. It's important to learn not only what the business aims for, but also what obstacles and regulatory hurdles may arise.
2. Align
The goal of this step is to unify strategy with objectives and actions, creating an integrated approach with senior leadership involvement and support for the decision-making process.
In simple words, this process needs:
Align business objectives with the strategy
Align executives with stakeholders' expectations
Align resource allocation planning with objectives
Alignment is most successful when you get buy-in at the top—ensuring senior management is truly committed to building a risk-aware culture. But don't stop there. Communicate the importance of GRC to everyone, emphasizing it as a shared responsibility across all levels. Set clear roles and responsibilities, defining who does what: from the board and CEO to the internal audit, IT, finance, and legal teams.
3. Perform
After aligning business goals and objectives, you need to perform. This step defines implementing proper controls and policies, preventing and remediating undesired risks, and monitoring to identify issues as soon as possible.
Here, practical measures come to the forefront. Use specialized GRC software tools to streamline compliance, monitor risk, and address operational shortcomings—whether it's a gap in third-party management or a challenge in regulatory reporting. Start by rolling out your GRC framework in a department or two, ensuring clarity and surfacing any significant issues before scaling up.
4. Review
As a final step, it's imperative to examine the design and operational performance of the existing strategy and actions. Moreover, this step encourages organizations to analyze goals to constantly enhance the integrated GRC activities.
Regular reviews ensure your GRC program keeps pace with changing risks, regulations, and business objectives. This iterative process is crucial for ongoing improvement, allowing you to fine-tune policies, strengthen controls, and keep your integrated approach robust and responsive.
What is the purpose of this model?
To design and maintain a steady and integral improvement process to achieve optimal performance and create value for your organization. By continuously learning, aligning, performing, and reviewing, you build a GRC strategy that is both resilient and adaptable—empowering your teams, supporting leadership, and positioning your business for long-term success.
Connect with our team and learn how you can design an integrated GRC program to strengthen your cybersecurity and protect your organization's value.







