Published on: Mar 29, 2024
Mastering NIST CSF 2.0 Framework Update - A Comprehensive Guide
The evolution of NIST CSF to its 2.0 version marks a big shift in the cybersecurity domain.
This article explores the critical updates and expanded capabilities of this framework, helping you understand and integrate it based on your unique organization's needs.
You'll learn how adopting NIST CSF 2.0 can enhance your security posture and also foster a culture of trust and compliance across all levels of your organization.
Let's get started!
Understanding the NIST Cybersecurity Framework (CSF)
What is the NIST CSF in a nutshell?
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a comprehensive approach designed to help organizations of all sizes and sectors enhance their cybersecurity measures. Yes, it's much more than just a set of guidelines.
At its core, the NIST CSF aims to provide a clear and accessible roadmap for improving digital security, helping businesses identify, protect against, detect, respond to, and recover from cybersecurity threats.
The Beginning of NIST CSF
From the start, the NIST CSF has offered organizations a thorough roadmap for effectively handling and minimizing cybersecurity threats. Born out of Executive Order 13636, known as "Improving Critical Infrastructure Cybersecurity," and initiated by former President Barack Obama in 2013, this framework has been regularly updated.
These updates ensure it stays ahead of new cyber dangers and keeps pace with the ever-changing world of business.
Back in 2014, when NIST CSF made its debut, it was a game-changer, designed to fortify the cybersecurity defenses of critical infrastructure. Think of it as the original blueprint that many sectors relied on to shape their cyber resilience strategies.
The adoption of the NIST CSF has become widespread across various sectors, ranging from government agencies to private enterprises. More importantly, organizations have leveraged its principles and guidelines to establish robust cybersecurity programs tailored to their specific needs, aligning with industry best practices and regulatory requirements.
Fast forward to today, and we've seen NIST CSF evolve into its 2.0 version. This is a transformation that reflects the collective wisdom and feedback from multiple industries.
Let's talk about what makes this framework great.
Why is NIST CSF a Game-Changer for Organizations?
It doesn't matter if you're in healthcare, finance, education, or running the infrastructure that keeps our world turning. The NIST CSF translates the complex language of cybersecurity into actionable insights that any organization can apply.
Here's what makes this framework stand out:
Framework Flexibility: Imagine a tool so versatile that whether you're a small non-profit or a multinational corporation, it fits your needs like a glove. That's the NIST CSF for you. It's crafted to adapt to the unique cybersecurity risks, size, and complexity of any organization.
Boosts Cybersecurity Postures: Implementing the NIST CSF is about empowering organizations not just to withstand cyber threats but to detect and neutralize them swiftly and efficiently.
Fosters Communication: Ever noticed how IT folks and the rest of the world sometimes seem to speak different languages? The NIST CSF bridges that gap, turning cybersecurity from a tech-only topic into a crucial conversation that includes everyone in the organization and extends to partners and stakeholders.
How CSF 2.0 Enhances Supplier and Partner Communication
CSF 2.0 plays a pivotal role in facilitating clear and effective communication with suppliers and partners. By setting defined cybersecurity standards, it aids organizations in aligning their communication strategies around cybersecurity risks. This ensures that everyone, from top executives to daily operations staff, shares a common understanding of security expectations and practices.
Furthermore, CSF 2.0 helps synchronize cybersecurity efforts with overall enterprise risk management strategies. This alignment makes it easier to engage in fruitful conversations about cybersecurity with external parties, ensuring that all stakeholders are on the same page.
Moreover, by integrating these practices across internal teams, companies can bolster their relationship with suppliers and partners. The framework ensures that cybersecurity discussions become a part of regular communication flows, thereby enhancing transparency and trust. This integration leads to more cohesive partnerships, as cybersecurity becomes a mutual priority for all involved.
What Drives NIST CSF 2.0 Changes?
First of all, it is important to highlight that the NIST CSF 2.0 is driven by several factors, such as:
Feedback and Stakeholder Input: NIST actively seeks feedback from stakeholders, including government agencies, industry experts, academia, and international partners, regarding the usability, effectiveness, and gaps within the existing framework.
Emerging Threat Landscape: The cybersecurity landscape is dynamic, characterized by the emergence of new threats, attack vectors, and vulnerabilities. NIST continuously monitors these developments and updates the CSF to ensure it remains aligned with current cybersecurity challenges and mitigation strategies.
Technological Advancements: Advances in technology, such as cloud computing, Internet of Things (IoT), artificial intelligence (AI), and quantum computing, introduce new complexities and risks to cybersecurity.
Regulatory and Legislative Changes: Regulatory requirements and legislative mandates related to cybersecurity may evolve, needing updates to the CSF to ensure alignment and compliance with applicable laws, regulations, and industry standards.
International Alignment: NIST collaborates with international partners and organizations to harmonize cybersecurity frameworks and standards across global boundaries. Updates to the CSF may reflect international best practices and align with frameworks developed by other countries or international bodies.
Related Topics and Activities
In addition to the driving factors, several related topics and activities are associated with the CSF 2.0, enhancing its applicability and user engagement:
Security and Privacy: These are at the core of the framework, encompassing general security measures, privacy protocols, and risk management strategies essential for safeguarding information.
Applications: The framework is applied through various methodologies, including the development of a robust cybersecurity framework tailored to different organizational needs.
Activities and Products: Practical tools such as quick-start guides and reference materials are available to facilitate the implementation of CSF 2.0, offering users a hands-on approach to understanding and leveraging the framework effectively.
Together, these factors and associated activities make the NIST CSF 2.0 a comprehensive and adaptable tool in the ever-evolving field of cybersecurity.
NIST CSF 2.0: Key Changes
The NIST CSF 2.0 has now 6 Functions broken down into 22 categories and 106 subcategories (as opposed to the 5 functions, 23 categories and 108 subcategories of the previous version). In general, the standard requirements were realigned and renamed to present a better structure and more prescriptive areas.
What about the new function?
The new Govern function encompasses the policies, procedures, and governance structures necessary to establish and maintain a robust cybersecurity program aligned with business objectives and risk tolerance.
Key aspects of the Govern function include:
Defining and communicating cybersecurity roles and responsibilities.
Establishing governance mechanisms to oversee and support cybersecurity initiatives.
Integrating cybersecurity into enterprise-wide risk management processes.
The CSF 2.0 also seeks to enhance communication with suppliers and partners. This is intended to help organizations seamlessly integrate cybersecurity-related issues with broader enterprise risk management strategies. By fostering improved collaboration, organizations can ensure that cybersecurity considerations are not siloed but are woven into the fabric of their overall risk management efforts.
This integration is crucial for identifying and mitigating potential threats across all aspects of the business. As a result, it enables a more resilient and adaptive approach to managing risks, ensuring that cybersecurity is a key component of strategic decision-making.
New Categories
Ten new categories were also included and, in most cases, there was just a realignment or old categories received new names:
Organizational Context (GV)
Risk Management Strategy (GV)
Roles, Responsibilities, and Authorities (GV)
Policies (GV)
Oversight (GV)
Cybersecurity Supply Chain Risk Management (GV)
Improvement (ID)
Identity Management, Authentication & Access Control (PR)
Platform Security (PR)
Technology Infrastructure Resilience (PR)
Incident Management (RS)
Now that we know what to expect from NIST CSF, let's go over the standard structure and its core functions.
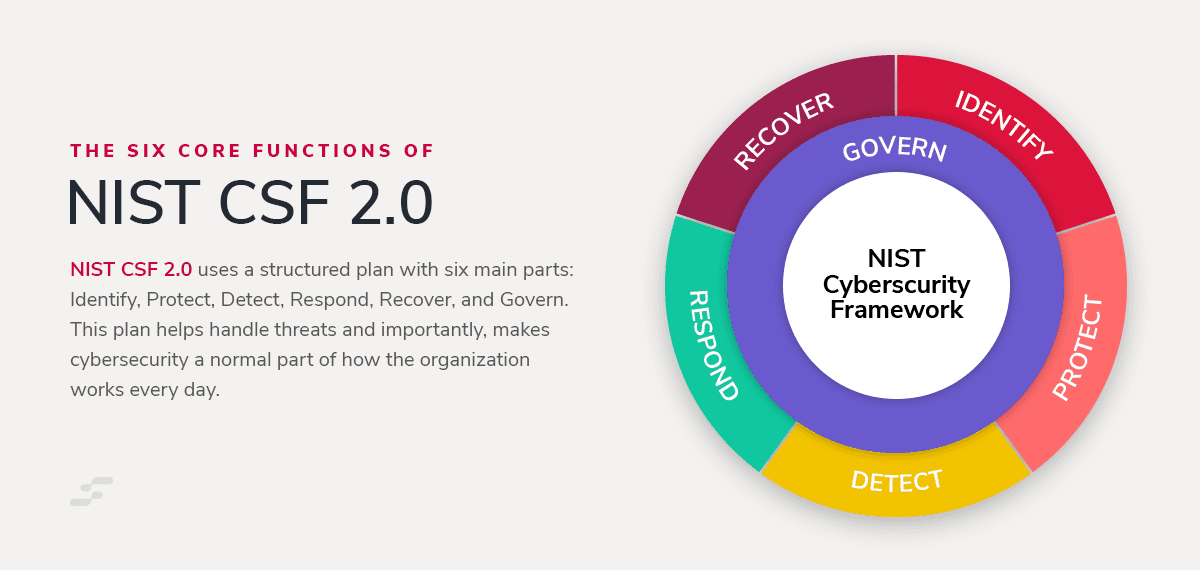
The Six Core Functions of NIST CSF 2.0
Something important to remember is that cybersecurity is more than a "technical challenge," it's a fundamental aspect of doing business.
The NIST CSF 2.0 responds to this reality with a structured approach, embodied in its six core functions: Identify, Protect, Detect, Respond, Recover, and Govern. This framework tackles threats; and more importantly, it integrates cybersecurity into the organizational core, making it a part of everyday operations.
These are the 6 levels of NIST CSF:
1. Identify
This is where it all starts. Before you can protect your organization, you need to know what you're protecting. This function helps you understand your digital environment, pinpointing the systems, assets, and data that are crucial to your operations. It's about making sure you have a clear map of your terrain.
2. Protect
With your map in hand, the next step is to fortify your defenses. This function focuses on implementing safeguards to ensure your critical services stay up and running, even in the face of cyber threats. It's about building the walls and defenses that keep your business safe.
3. Detect
A strong defense is vital, but you also need to know when it's being tested. The Detect function is your surveillance system, designed to quickly spot any signs of a cybersecurity event. It's your lookout on the tower, keeping an eye out for trouble on the horizon.
4. Respond
Despite your best efforts, breaches can happen. The Respond function is your action plan for when they do. It outlines how to manage and mitigate the impact of a cybersecurity incident. Think of it as your emergency response team, ready to jump into action at a moment's notice.
5. Recover
After a storm, it's time to rebuild. The Recover function helps you restore any services or capabilities that were impaired during an incident. It's about getting back on your feet, repairing the damage, and learning from the experience to come back stronger.
6. Govern
The new kid on the block, the Govern function, ties everything together. It emphasizes the importance of leadership and governance in managing cybersecurity risks. This isn't about adding more red tape; it's about ensuring that everyone from the boardroom to the IT department is on the same page. Working together to safeguard the organization.
By integrating these six functions, NIST CSF 2.0 provides a comprehensive and cohesive approach to managing cybersecurity risks. The goal here is to have a clear plan, staying vigilant, responding swiftly when necessary, and always striving for improvement.
How to Seamlessly Implement NIST CSF 2.0 in Your Organization
Implementing the NIST Cybersecurity Framework (CSF) 2.0 is a strategic move towards bolstering your organization's cybersecurity defenses. NIST has rolled out a suite of new tools and resources tailored to assist organizations in navigating and adopting the framework efficiently, focusing on governance and supply chain security enhancements.
Let's start with some practical steps for adoption:
Evaluate Your Current Landscape: Begin by understanding where you currently stand. It's akin to taking stock of puzzle pieces you already have.
Define Your Cybersecurity Ambitions: Clearly outline what you aim to achieve. Imagine what the completed puzzle should look like.
Spot the Missing Pieces: Identify gaps between your current state and the desired outcome. These are the puzzle pieces you're missing.
Craft Your Strategy: Plan your approach to find these missing pieces. This is your puzzle-solving strategy.
Put the Puzzle Together: Start implementing changes, focusing on areas that get you closer to the complete picture.
Review and Adjust: Step back occasionally to see if the puzzle is coming together as expected. Adjust your strategy as needed.
Now, let's review some of the tools at your disposal!
NIST's Toolkit
NIST's toolkit for CSF 2.0 offers a range of resources designed to streamline the framework's adoption and integration.
Let's go over some of them:
NIST Cybersecurity Framework reference tool: This new reference tool simplifies navigating the CSF, allowing users to easily browse, search, and export data from the framework's guidance in formats that are both human-friendly and machine-readable.
Informative Reference Catalog: With a searchable catalog that facilitates cross-referencing the CSF's guidelines with over 50 other cybersecurity documents, such as NIST SP 800-53, organizations can streamline compliance across multiple standards.
Community Profiles: Understanding how similar organizations apply the CSF can be incredibly valuable. NIST's community profiles showcase diverse implementation strategies across various industries, providing real-world examples of framework adaptation.
Implementation Examples: Catering to the varied needs of different organizations, NIST offers detailed guidance, including linkages and mappings to specific cybersecurity guidance from NIST and other bodies. These practical examples furnish clear directions for starting and refining your cybersecurity strategy.
Quick Start Guides: Designed with small businesses, risk managers, and supply chain security in mind, these guides offer targeted advice for quick and effective framework adoption.
Integration Tips:
Leverage Available Tools: Utilize NIST's tools to make the framework adoption more straightforward and tailored to your organization's needs.
Engage Across the Organization: Successful implementation requires buy-in and participation from all organizational levels, not just IT.
Build Upon Existing Practices: Integrate CSF 2.0 enhancements with your current cybersecurity measures to reinforce your defense strategy.
Prioritize Flexibility and Adaptability: As threats evolve, so should your cybersecurity practices. Stay informed and ready to adjust your strategies.
Implementing NIST CSF 2.0 is about building a cybersecurity picture that aligns with your organization's unique landscape. With the right approach and resources, you'll enhance your security posture and also build a resilient, compliant, and forward-thinking cybersecurity strategy.
Now, what if you already implemented NIST CSF?
How to Transition to NIST CSF 2.0
This update is all about transferring what works, adjusting what doesn't, and making the most of new opportunities for improvement and growth.
Steps for a Smooth Transition:
Conduct a Comparative Analysis: Start by comparing your current alignment with CSF 1.x against the new elements and structure of CSF 2.0. Identify key differences and potential gaps in your cybersecurity practices.
Engage with New CSF 2.0 Resources: NIST offers an array of tools designed to ease this transition. Familiarize yourself with the updated resources to fully leverage the enhancements in CSF 2.0.
Update Your Organizational Profile: Reflect on how changes in CSF 2.0 impact your organizational profile. This profile should evolve to encapsulate new risk management strategies and objectives aligned with CSF 2.0.
Key Considerations for Updating:
Understand the 'Govern' Function: CSF 2.0 introduces the Govern function, emphasizing governance in cybersecurity risk management. Ensure your transition plan incorporates this critical focus.
Review and Adapt to New Categories and Subcategories: CSF 2.0 has refined and added categories and subcategories. Review these changes meticulously to ensure your cybersecurity framework remains comprehensive and aligned.
Leverage the Informative References: These references are vital for understanding the specific changes and how they relate to other standards and frameworks. They serve as a roadmap for integrating CSF 2.0 into your cybersecurity strategy.
Implementing the Transition:
Prioritize Based on Impact: Not all changes will have the same level of impact on your organization. Prioritize updates that offer the most significant benefit to your cybersecurity posture.
Communicate Changes: Keep all stakeholders informed about how the transition affects them. Clear communication ensures buy-in and facilitates smoother implementation.
Train Your Team: Ensure that everyone involved understands CSF 2.0, especially new concepts and approaches introduced in this update. Consider formal training or workshops to bring your team up to speed.
Enhancing Trust and Compliance Through NIST CSF 2.0
Adopting NIST CSF 2.0 represents a pivotal strategy for organizations looking to elevate their cybersecurity posture. This framework goes beyond mitigating risks; it's a commitment that resonates with clients and stakeholders, enhancing trust and ensuring compliance amidst a landscape of evolving regulations.
Building Trust with Clients and Stakeholders
By integrating NIST CSF 2.0, organizations demonstrate a proactive approach to safeguarding sensitive data, a move that significantly boosts their credibility. This level of dedication to cybersecurity is quickly becoming a deciding factor for clients and stakeholders when choosing whom to trust with their business.
In an era where data breaches are not just common but also costly, showcasing a robust cybersecurity framework aligned with NIST CSF 2.0 can set an organization apart as a trusted partner.
Ensuring Compliance in a Shifting Regulatory Environment
The framework's comprehensive coverage of cybersecurity essentials helps organizations not only meet current standards but also adapt to new regulations as they come. This adaptability is crucial for maintaining a compliant stance, especially in sectors where regulatory demands are stringent and constantly changing.
The NIST CSF 2.0 facilitates a structured approach to compliance, making it easier for businesses to navigate the complexities of cybersecurity regulations and standards.
Real-World Impact and Market Differentiation
Examples of NIST CSF 2.0's positive impact on organizations abound, illustrating how alignment with the framework can lead to strengthened customer relationships and a notable market advantage:
A regional bank, after implementing NIST CSF 2.0, reported an increase in client trust, attributed to their transparent communication about enhanced cybersecurity measures. This trust translated into a higher retention rate and attracted new clients looking for secure banking solutions.
A healthcare technology company found that aligning with NIST CSF 2.0 not only streamlined their compliance with HIPAA regulations but also served as a key differentiator in their market. Their commitment to data security, validated by adherence to the framework, became a compelling selling point in contracts and proposals, setting them apart from competitors.
In essence, NIST CSF 2.0 is more than a set of guidelines—it's a strategic framework that can significantly impact an organization's trustworthiness, compliance posture, and market positioning.
Through its adoption, businesses not only safeguard against cyber threats but also solidify their reputation as secure and reliable entities, fostering stronger relationships with clients and achieving differentiation in their respective industries.
Customization and Flexibility of NIST CSF 2.0
NIST CSF 2.0 isn't a one-size-fits-all solution. Its real power lies in its adaptability, allowing organizations of all sizes and sectors to tailor it to their unique cybersecurity needs and maturity levels.
This flexibility is crucial for developing a cybersecurity strategy that not only addresses specific operational challenges but also evolves with the organization.
Tailoring the Framework to Your Organization
The NIST CSF 2.0 is designed with customization in mind. Here's how organizations can make the most of this flexibility:
Assess Your Cybersecurity Maturity: Start by evaluating your current cybersecurity practices against the framework. This initial assessment will help you understand your organization's maturity level and pinpoint areas for improvement.
Identify Specific Needs: Every organization faces unique cybersecurity challenges. Identify yours by considering factors like your industry, size, and the nature of the data you handle. This will guide your customization of the framework.
Set Priorities: Based on your assessment and specific needs, prioritize the framework's functions and categories that align most closely with your most pressing challenges.
Adapt and Implement: Use the prioritized elements to adapt the framework to your context. Implement changes gradually, focusing on areas that will have the most significant impact on your cybersecurity posture.
Review and Adjust Regularly: The cyber threat landscape is constantly changing, and so should your cybersecurity strategy. Regularly review your implementation of the NIST CSF 2.0, adjusting as necessary to address new challenges and opportunities.
Key Takeaways
The updated framework provides a comprehensive roadmap for enhancing cybersecurity practices across all sectors, ensuring organizations are well-equipped to protect against and respond to cyber threats.
NIST CSF 2.0 is designed to be adaptable, allowing organizations to tailor the framework to their unique needs and cybersecurity maturity levels, ensuring a personalized approach to digital security.
Adopting the framework not only bolsters your cybersecurity defenses but also enhances trust among stakeholders and ensures compliance with evolving regulations, fostering a secure and compliant business environment.
NIST offers an array of tools and resources, including a new reference tool and quick start guides, to facilitate the framework's seamless integration into existing cybersecurity practices.
The adoption of NIST CSF 2.0 signifies a commitment to advanced cybersecurity management, offering a strategic advantage in building stronger customer relationships and achieving market differentiation.
Incorporating NIST CSF 2.0 into your cybersecurity strategy is not just about meeting standards—it's about setting a new benchmark for security, resilience, and trust in an increasingly digital world.
Book a demo with our team to learn how StandardFusion helps you simplify the management of frameworks like NIST CSF 2.0, making it easier for your organization to adopt, customize, and maintain compliance with confidence.







