Published on: Aug 15, 2022
How HIPAA, HITRUST CSF, and NIST CSF Boost Cybersecurity in Healthcare
Over the past decade, healthcare has undergone a massive digital transformation. The rise of electronic records, telemedicine, and smart medical devices has brought undeniable advantages to both patients and providers—enhancing convenience, improving outcomes, and streamlining care delivery.
But with great innovation comes great risk.
Technology and convenience don’t always align with strong security practices. Unfortunately, cybersecurity is often an afterthought—leaving healthcare organizations vulnerable to threats that can compromise sensitive data and patient trust.
That’s why we’ve created this simplified guide—to help you understand how frameworks like HIPAA, HITRUST CSF, and NIST CSF work together to secure healthcare data and support compliance.
Let's jump right in!
Why HIPAA Cybersecurity Frameworks Matter
Healthcare organizations handle vast amounts of sensitive data daily. Implementing a cybersecurity framework aligned with HIPAA is no longer optional—it’s essential.
Safeguarding Patient Information
At its core, HIPAA is about protecting Protected Health Information (PHI) and Electronic PHI (ePHI). It requires organizations to put safeguards in place that prevent unauthorized access and ensure patient data remains confidential.
Ensuring Integrity and Availability
In addition to confidentiality, HIPAA emphasizes data integrity and availability. That means keeping patient information accurate, consistent, and accessible when needed—all while preventing breaches that could endanger care delivery.
Staying Ahead of Emerging Threats
As technology evolves, so do cyber threats. Healthcare providers must be proactive—continually updating cybersecurity measures to defend against increasingly sophisticated attacks.
Building Trust Through Compliance
Complying with HIPAA doesn’t just help you avoid penalties—it also builds patient confidence. When patients trust their data is safe, they’re more willing to share sensitive information critical to their care.
Bottom line? Adopting a strong cybersecurity framework aligned with HIPAA is a strategic necessity for any healthcare organization.
The State of Healthcare Data Security
Healthcare is one of the most targeted—and most breached—industries in the world. Between 2015 and 2019, the healthcare sector led in data breaches. More recently, IBM reported that the average cost of a healthcare data breach has soared to $9.23 million globally. More than any other industry.
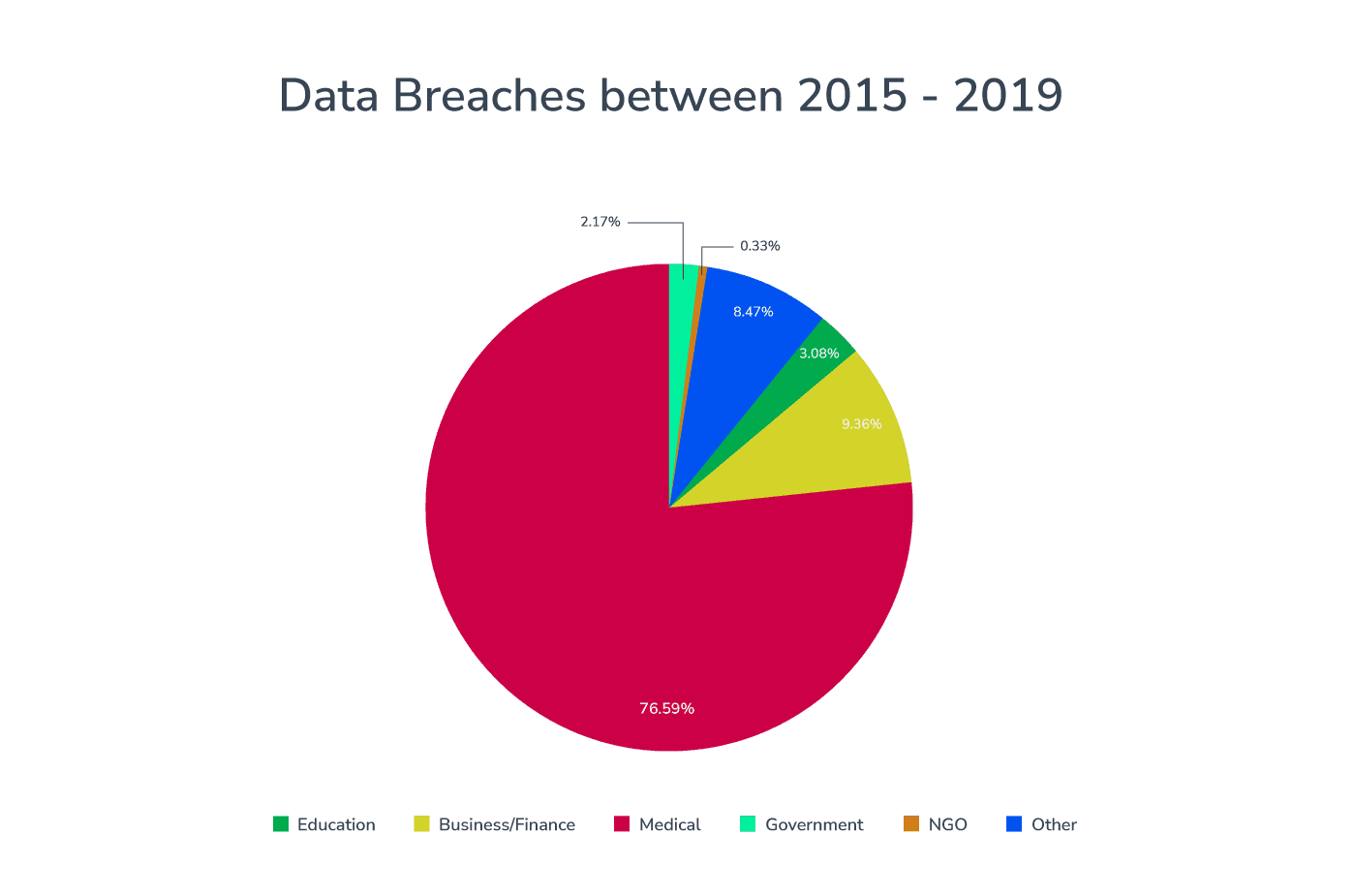
Does that mean healthcare has the weakest cybersecurity?
Not necessarily. The healthcare industry holds a vast quantity of highly valuable data, making it a prime target for cybercriminals. The more data you store, the more appealing you become to attackers.
To address these challenges, the Health Insurance Portability and Accountability Act (HIPAA) was enacted in 1996. It set the foundation for protecting patient data and introduced penalties for noncompliance—encouraging the healthcare industry to take data security seriously.
What HIPAA Covers—and What It Doesn’t
HIPAA outlines a set of administrative, physical, and technical safeguards designed to protect ePHI based on the CIA triad: Confidentiality, Integrity, and Availability.
Key HIPAA Rules
Privacy Rule: Limits how PHI is shared and ensures patient consent.
Security Rule: Specifies how PHI should be protected during transmission, storage, and processing.
Enforcement Rule: Establishes penalties for noncompliance.
Breach Notification Rule: Requires affected parties to be notified of a breach within 60 days.
Minimum Necessary Rule: Limits PHI access to only what is required for a task.
But There’s a Catch...
HIPAA is deliberately vague about how to implement these controls. For instance, it might suggest encryption but doesn’t specify what kind, how, or when. While this allows flexibility, it also leads to inconsistent implementation and confusion—especially when assessing vendor compliance.
A healthcare organization may outsource services to dozens of vendors, each interpreting HIPAA differently. The result? A patchwork of inconsistent audit reports that make compliance verification a nightmare.
Why Additional Frameworks Are Necessary
To bridge HIPAA’s ambiguity, security frameworks like the NIST Cybersecurity Framework (CSF) and HITRUST CSF provide much-needed structure. They define concrete controls, align with industry best practices, and simplify compliance assessments.
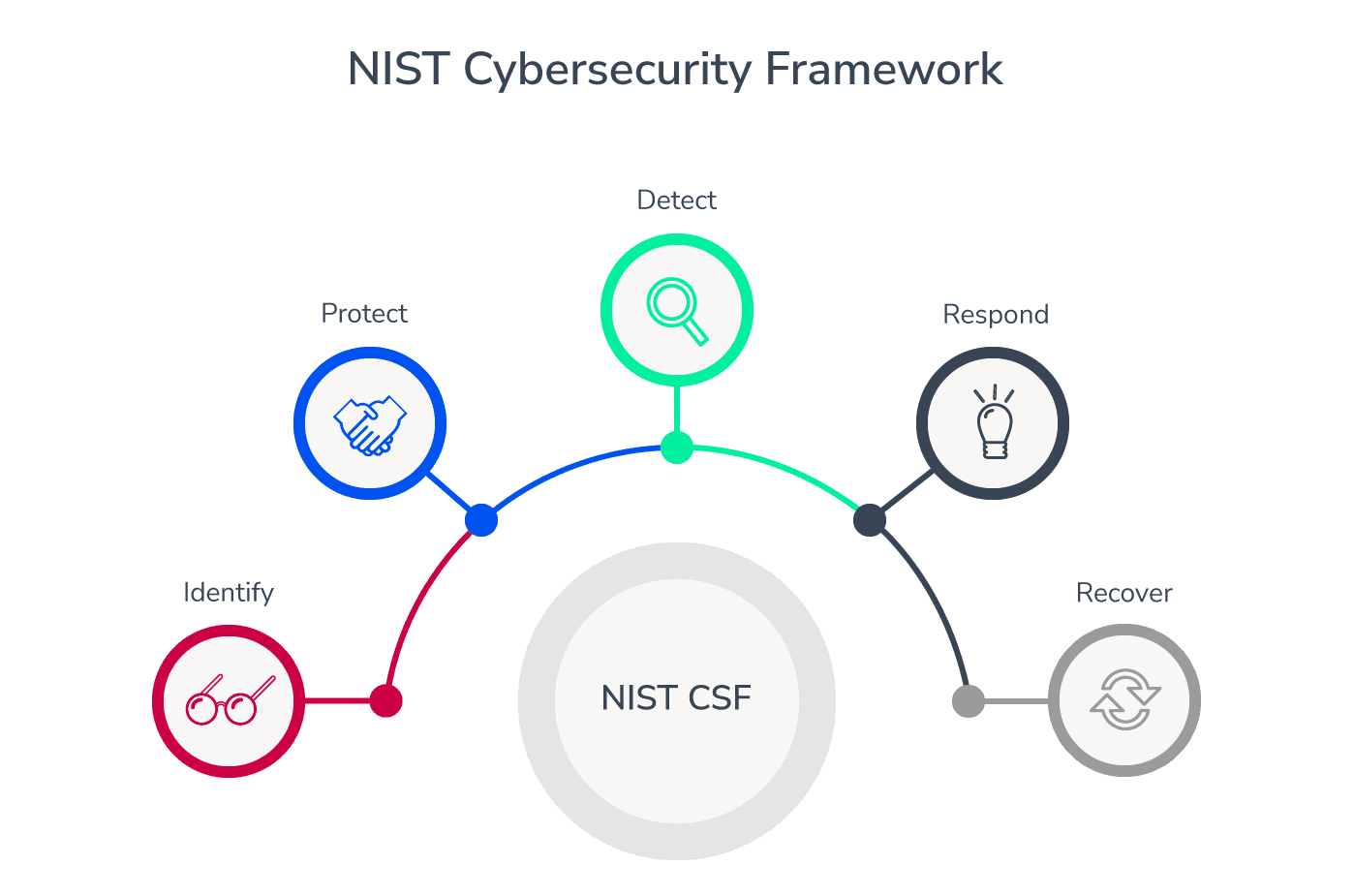
How the NIST CSF Supports Data Protection
The NIST CSF is a widely adopted framework structured around five core functions that help organizations manage and mitigate cybersecurity risk:
Identify – Understand and manage cybersecurity risks across systems, assets, data, and people.
Protect – Implement safeguards to ensure delivery of critical services and reduce the impact of potential incidents.
Detect – Establish capabilities to identify cybersecurity events promptly.
Respond – Develop plans and actions to contain and mitigate cybersecurity incidents.
Recover – Build resilience and restore capabilities affected by a cybersecurity incident.
Each function includes categories and subcategories that guide organizations toward specific cybersecurity outcomes. These align closely with HIPAA’s goals for protecting PHI.
Diving Deeper: NIST SP 800-53 and Risk Assessments
For detailed control guidance, NIST Special Publication 800-53 offers hundreds of specific controls, while NIST SP 800-30 provides a risk assessment methodology to:
Identify potential threats and vulnerabilities
Assess their likelihood and impact
Prioritize mitigation strategies based on risk levels
While NIST CSF doesn’t guarantee HIPAA compliance, it serves as a strong foundational framework to guide security investments and control implementations.
Enter HITRUST CSF: Bridging the Gap Between Frameworks and Compliance
Maintaining compliance with multiple frameworks can be complex and resource-intensive. That’s where the HITRUST Common Security Framework (CSF) comes in.
Originally created to simplify HIPAA compliance, HITRUST CSF has since evolved to incorporate and harmonize multiple standards—including NIST CSF, HIPAA, ISO 27001, GDPR, PCI-DSS, and more.
HITRUST: A Common Framework with Broad Benefits
Provides a certifiable path to compliance
Maps controls to multiple frameworks
Simplifies vendor risk assessments
Offers detailed guidance where HIPAA falls short
Does HITRUST Equal HIPAA Compliance?
Theoretically, yes. If your HITRUST implementation is comprehensive and well-executed, it can serve as proof of compliance with HIPAA—and NIST CSF as well.
That’s why HITRUST has become the gold standard in healthcare cybersecurity..
A Unified Security Strategy: Better Protection, Easier Compliance
An integrated security approach—combining HIPAA, NIST CSF, and HITRUST—helps healthcare organizations:
Ensure regulatory compliance
Streamline risk assessments
Improve incident response and recovery
Proactively secure sensitive data
Build trust with patients and partners
The Benefits Don’t Stop There:
Continuous improvement through regular updates and assessments
Audit readiness with mapped controls and centralized documentation
Future-proofing against evolving threats and regulations
One Framework to Rule Them All?
Yes, adopting comprehensive frameworks like HITRUST CSF may seem overwhelming at first. But the benefits far outweigh the effort.
By embracing a robust security strategy that aligns with HIPAA and integrates best practices from NIST CSF and other standards, your organization is better positioned to reduce risk, improve compliance, and protect what matters most—your patients.
Let StandardFusion Help
At StandardFusion, we build holistic, all-in-one, enterprise-grade GRC software designed to simplify risk and compliance management.
Our platform enables you to:
Manage policies, audits, and vendors
Streamline HITRUST CSF implementation
Map controls across HIPAA, NIST CSF, ISO 27001, and SOC 2
Generate audit-ready reports and insights on demand
Compliance doesn’t have to be complicated.
Let us show you how to make it easier. Reach out to our team today.







