Published on: Jul 29, 2017
FedRAMP Impact Levels Low, Moderate, and High. What's the Difference?
Becoming certified under the Federal Risk and Authorization Management Program (FedRAMP) is a costly and resource intensive undertaking. Obtaining certification and continually staying in compliance can make a major impact on your business as a Cloud Service Provider (CSP).
To lessen the costly and time-consuming process, FedRAMP utilizes a "do once, use many times" Security Assessment Framework (SAF). This approach helps reduce redundancies when conducting security assessments and process monitoring reports.
As part of FedRAMP's effort to streamline compliance, their SAF is standardized into four process areas: Document, Assess, Authorize, and Monitor. Within the Document process area, FedRAMP asks CSPs to determine what types of data they are managing and complete a FIPS PUB 199 worksheet. This step is crucial for categorizing your systems and assessing the impact level of your information.
To aid in this process, CSPs can consult several key resources. The FIPS 199 publication is essential, as it provides guidelines for categorizing types of information and information systems according to security impact levels. Additionally, the NIST SP 800-60 offers a comprehensive guide to mapping information types to security categories. These documents, though extensive, are foundational for understanding and implementing security standards.
Given the complexity and volume of these government publications, they can be daunting. For a more streamlined approach, consider leveraging platforms designed to assist with compliance across various frameworks like FedRAMP, NIST SP 800-171, CMMC, HIPAA, and ISO 27001. Such platforms can help you determine necessary security controls, identify potential redundancies, and simplify your path to certification.
By integrating these resources and tools, CSPs can efficiently navigate the requirements and ensure they accurately assess their impact levels, ultimately facilitating their journey toward achieving compliance.
What is FIPS 199 Worksheet?
FedRAMP didn't create these categorization levels. Instead it borrows from the Federal Information Processing Standard (FIPS) which was developed by the National Institute of Standards and Technology (NIST). Here they've defined three ways of securing data according to Confidentiality, Availability, and Integrity.
To better understand these levels, consider how FIPS 199 defines the three levels of impact for cloud service providers:
Security Objective | Potential Impact | ||
|---|---|---|---|
LOW | MODERATE | HIGH | |
Confidentiality Integrity Guarding against | The unauthorized | The unauthorized | The unauthorized |
Integrity Guarding against improper | The unauthorized | The unauthorized | The unauthorized |
Availability Ensuring timely and reliable | The disruption of access to | The disruption of access to | The disruption of access to |
As you can see in the above chart, there are three FedRAMP impact levels: Low, Moderate, and High. Deciding which set of control requirements to follow depends on the kinds of data you are managing and the different modes of securing and protecting that data. Each subsequent impact level requires additional controls to ensure that your data is adequately protected.
To fully understand how these impact levels are determined, consider the three axes of impact:
Confidentiality: This axis focuses on preserving restrictions on sensitive information access and disclosure. It aims to protect personal and proprietary information, ensuring privacy is maintained.
Integrity: This involves maintaining information accuracy within the system, guarding against unauthorized access, destruction, or modification. It also includes verifying the authenticity of information, ensuring it remains trustworthy and reliable.
Availability: While often overlooked, availability is crucial. It ensures that information can be accessed and used reasonably and timely, only by authorized personnel. Imagine storing all information in a secure but inaccessible black box—it would be safe but useless when needed.
The impact level on each axis dictates the minimum security controls required. If a cloud service provider has a high impact level in any of these areas, it sets the minimum required standard across all axes. This ensures that the provider meets rigorous security demands, safeguarding data from potential threats.
Understanding how these axes interact and influence FedRAMP certification is vital for any cloud service provider seeking compliance. It highlights the importance of not only securing data but also making it accessible to those who need it while maintaining integrity and confidentiality.
Understanding the FedRAMP Certification Process for Cloud Providers
When you're a cloud services provider looking to collaborate with the U.S. Government, gaining FedRAMP (Federal Risk and Authorization Management Program) certification is a crucial step. This certification ensures that your services meet rigorous government security standards.
Step 1: Understand Your Systems and Purpose
Start by comprehensively understanding your systems, your intended purpose with government agencies, and the types of data you will handle. This helps in determining the impact level—high, moderate, or low—of your services. The impact level dictates the security controls you need to implement.
Step 2: Assess Your Impact Level
To assess the impact level, refer to government resources like the Federal Information Processing Standards (FIPS) 199 and NIST Special Publication 800-60. These documents guide you in mapping your information and systems to appropriate security categories. However, they are extensive and may contain sections not pertinent to your services.
Step 3: Implement Security Controls
Once you've identified your impact level, you must implement the necessary security controls. This involves considering how you handle and store information. Sometimes, restructuring your services to minimize data handling can shift your impact level from high to moderate, or even to low.
Step 4: Choose a Framework
Depending on your operational needs, you might also aim for alignment with other frameworks like NIST SP 800-171, CMMC, HIPAA, or ISO 27001. Each comes with specific compliance requirements, but understanding FedRAMP first gives a solid foundation.
Step 5: Leverage Automation Tools
The certification process can be daunting, but automation tools and platforms can streamline the categorization of your systems, help determine necessary security measures, reduce redundancy, and facilitate the compliance journey. Such tools offer a more practical approach than manually sifting through hundreds of pages of standards.
Step 6: Prepare for Review and Authorization
After ensuring all necessary controls are implemented and documented, your system will undergo a thorough review process. A third-party assessor will check compliance with FedRAMP requirements. If everything is in order, your service receives provisional authorization, allowing you to begin operations with federal agencies.
Ultimately, gaining FedRAMP certification not only opens doors to government contracts but also enhances your service's credibility and increases trust with clients across sectors.
Is your Data Low, Moderate, or High Security Impact?
Figuring out which FedRAMP impact levels your Cloud Service Offering (CSO) should follow is critical to the compliance process.
Low Impact Security Level
A low impact level involves data that, if compromised, would cause minimal harm. For example, information such as your name, phone number, or email address falls into this category. While a breach might lead to more spam or robocalls, the overall risk remains low because this information is widely available through other channels.
Confidentiality: Unauthorized disclosure of this data is expected to have a limited adverse effect on organizational operations, assets, or individuals.
Integrity: Any unauthorized changes or destruction of information would similarly have minimal adverse effects.
Availability: Disruptions in accessing or using this information are also expected to have a limited impact.
Understanding Li-SaaS
Li-SaaS, or Low Impact Software as a Service, is a specialized control set designed for systems that handle limited data. Specifically, these systems only manage minimal Personally Identifiable Information (PII) necessary for login purposes and nothing more. This focused approach means that even if a system breach occurs, the impact remains minimal.
Connection to Low Impact Services
The concept of Li-SaaS is tailored to cloud services with lower data sensitivity and operational impact. This unique framework offers two primary advantages:
Streamlined Authorization: For services with a low baseline of data sensitivity, Li-SaaS facilitates a more rapid authorization process. This fast-tracked approach saves time while maintaining essential security standards.
Selective Security Validation: Unlike higher impact services, which undergo extensive evaluations, Li-SaaS allows agencies to concentrate on validating the most critical security controls. Instead of a full-scale audit, a targeted review ensures that core protections are in place, enhancing efficiency without compromising security.
In essence, Li-SaaS provides a pragmatic pathway for cloud service providers operating at a lower risk level, ensuring they meet appropriate security measures without unnecessary complexity.
Moderate Impact Security Level
The moderate security level baseline is required if your data includes personally identifiable information (PII). If this information system is compromised, it would have a serious impact.
Moderate impact cloud services are crucial for organizations that work with sensitive information, often involving government-related data that is not publicly available. This data may not be classified, but its compromise could significantly affect the organization and its personnel.
Confidentiality: Unauthorized disclosure could seriously affect operations, assets, or individuals.
Integrity: Unauthorized modification or destruction could also have serious adverse effects.
Availability: Disruption of access or use could lead to significant operational impacts.
The moderate impact level is the most common category because it covers a wide range of services. From small-scale data access to managing vast amounts of important data, this category encompasses nearly 80% of cloud service providers that receive federal authorization. Although a compromise might lead to injuries, it does not result in loss of life, underscoring its critical but non-lethal level of impact.
Why is the Moderate Impact Level the Most Common Category in FedRAMP?
The Moderate impact level stands as the most prevalent category in FedRAMP for several key reasons. First, its scope is extensive enough to include a wide range of services. This level caters to cloud providers managing a spectrum of sensitive data, from minimal to substantial volumes.
Broad Applicability
The Moderate impact level is versatile. It covers cloud services that deal with crucial, but not highly sensitive, information, making it an ideal fit for many organizations. Whether a provider accesses small fragments of critical data or handles vast amounts, this category offers the flexibility they need.
Volume of Providers
A significant number—nearly 80%—of cloud service providers attain FedRAMP authorization at this level. This sheer volume underscores how this category is particularly suitable for most providers, allowing them to secure government contracts while managing their resources efficiently.
Balance of Security and Accessibility
The Moderate level strikes a balance between stringent security measures and sufficient accessibility. It ensures that cloud services adhere to necessary security protocols without the exhaustive requirements that higher levels might demand. This makes it an attractive choice for providers that need to maintain a strong security posture without overextending their resources.
In summary, the Moderate impact level's broad applicability, high adaptability, and balanced approach to security and accessibility make it the go-to choice for most cloud service providers seeking FedRAMP authorization.
High Impact Security Level
High impact encompasses critical personal data such as your social security number or passport details. A breach at this level could result in severe identity theft, with cascading effects that can severely disrupt lives. In a governmental context, this might involve accessing critical operations, posing a threat to national security.
Confidentiality: Unauthorized disclosure could cause severe or catastrophic effects, threatening national security or critical infrastructure.
Integrity: Unauthorized modifications could result in catastrophic consequences, affecting national operations and individual safety.
Availability: The inability to access or use this information could lead to severe disruptions, impacting essential services and possibly resulting in loss of life.
Certification Requirements for Moderate and High Impact Levels
Unlike the streamlined approach available at the low impact level, achieving FedRAMP certification for both moderate and high impact environments involves a comprehensive process. Providers must undergo a full assessment, demonstrating compliance with every security control relevant to their impact category.
This means:
Complete Security Assessments: Every applicable security control—often numbering in the hundreds—must be thoroughly evaluated by a Third Party Assessment Organization (3PAO), such as Coalfire or Schellman.
Full Documentation and Continuous Monitoring: Service providers are required to maintain detailed security documentation and implement robust continuous monitoring to ensure ongoing compliance.
No Shortcuts or Reduced Scopes: Unlike with Li-SaaS at the low level, there are no abbreviated review paths. Each control, safeguard, and requirement must stand up to scrutiny at the moderate or high threshold.
This rigorous process ensures that cloud services operating at these levels provide strong protection for sensitive or mission-critical government data before they can support federal workloads.
From Low to High: Increasing Number of Controls
Higher security levels require additional security controls, such as higher levels of authentication for people to enter, access, and gain control of these systems. This means more, and increasingly secure ways of determining if the person with access is who they claim to be. This also means ensuring upgraded procedures of validating this information as well as determining what they can have access to and what they can do with this data.
High-Impact Systems
For high-impact systems, some key aspects recommended by FedRAMP include the reduction of human error as much as possible, often done by the means of automation. FedRAMP also suggests guaranteeing that the entire scope of authorization already encompasses the full spectrum of services.
Low-Level Systems
Low-level systems have exactly 125 controls, moderate level systems have 325 controls, while high-level systems are required to comply with 421 controls. With the three levels in place, any federal agency can now store highly sensitive data on any provider of cloud services as long as they are FedRAMP compliant.
To effectively adhere to these security controls, cloud service providers must first determine their impact level. This involves a thorough understanding of their systems, the purpose of their engagement with government entities, and the type of information they will handle. The impact level dictates the necessary security measures, making it crucial to categorize information accurately.
Providers can reference FIPS 199 and NIST SP 800-60, which are essential guides for mapping information and systems to security categories. While these documents are comprehensive, they can be overwhelming due to their extensive standards and definitions.
For a more streamlined approach, providers can leverage comprehensive platforms that assist in categorizing systems, determining necessary controls, and minimizing redundancies. This not only aids in accurately assessing impact levels but also enhances the efficiency of achieving FedRAMP compliance.
Takeaway
Understanding these levels is crucial for cloud service providers tasked with safeguarding data. The standards they follow must match the potential impact of a breach. A service managing only contact details differs significantly from one handling sensitive operations for federal agencies. This delineation underscores the need for tailored security measures aligned with the impact level to protect both individuals and broader governmental functions.
Lowering the Impact Level for FedRAMP: A Guide for Cloud Providers
For cloud providers aiming to obtain FedRAMP certification, understanding how to potentially lower their impact level is crucial. Here’s how you can achieve that:
Understand Your Systems and Purpose
Assess Your Systems: Begin by thoroughly analyzing your current infrastructure and the services you offer. Identifying the types of data you handle is essential.
Define the Government Role: Clearly understand your intended purpose in government projects. This clarity helps in knowing the specific data and functional requirements.
Determine Information Sensitivity
Once you've assessed your systems, evaluate the sensitivity of the information you're handling. This evaluation will help you determine the required security protocols.
Implement Security Controls Appropriately
Security levels are directly related to the data's sensitivity. You can streamline your security processes by:
Minimizing Data Collection: Collect and process only the necessary data to fulfill your service obligations.
Re-engineering Services: Consider redesigning certain processes to handle less sensitive or less voluminous data.
These adjustments not only safeguard your systems but can also potentially lower your impact level from high to moderate, or moderate to low. This recalibration can make compliance more straightforward and less resource-intensive.
Re-evaluate Periodically
Finally, make it a practice to regularly revisit and review your data handling practices. Ensure you're consistently aligning with only the essential data flow to maintain or reduce your impact level effectively.
By systematically analyzing and adjusting how you handle data, cloud providers can efficiently work towards a lower impact level, facilitating a smoother FedRAMP certification process.
Why is Availability Crucial in Determining Impact Levels?
When considering impact levels in information security, availability plays a pivotal role. Imagine storing all your data in a vault that's virtually impregnable—safe from prying eyes and unauthorized access. This setup seems ideal until you realize that if nobody, not even authorized users, can access this information when needed, it's utterly useless.
The Importance of Availability:
Usability of Information: Information that cannot be accessed effectively serves no purpose. Availability ensures that data and resources are accessible to the right people at the right time, allowing for informed decision-making and efficient operations.
Balancing Security and Accessibility: While it's essential to maintain robust security measures, they shouldn't hinder legitimate access. Availability strikes the balance, ensuring that security protocols don’t become obstacles for those who genuinely need the information.
Support for Critical Operations: Many industries, such as healthcare and finance, depend on the timely access to data. Unavailability can lead to substantial operational bottlenecks or even critical failures, affecting everything from patient care to financial transactions.
Business Continuity: In the event of a crisis or disaster, the ability to access information promptly determines how quickly a company can recover. Availability ensures that systems stay operable, supporting continuous service delivery.
Availability is the backbone supporting the functionality and efficiency of information systems. It allows businesses to operate smoothly and effectively, bolstering overall security by ensuring the rightful flow of information where it's needed most.
Breakdown of FedRAMP Control Types
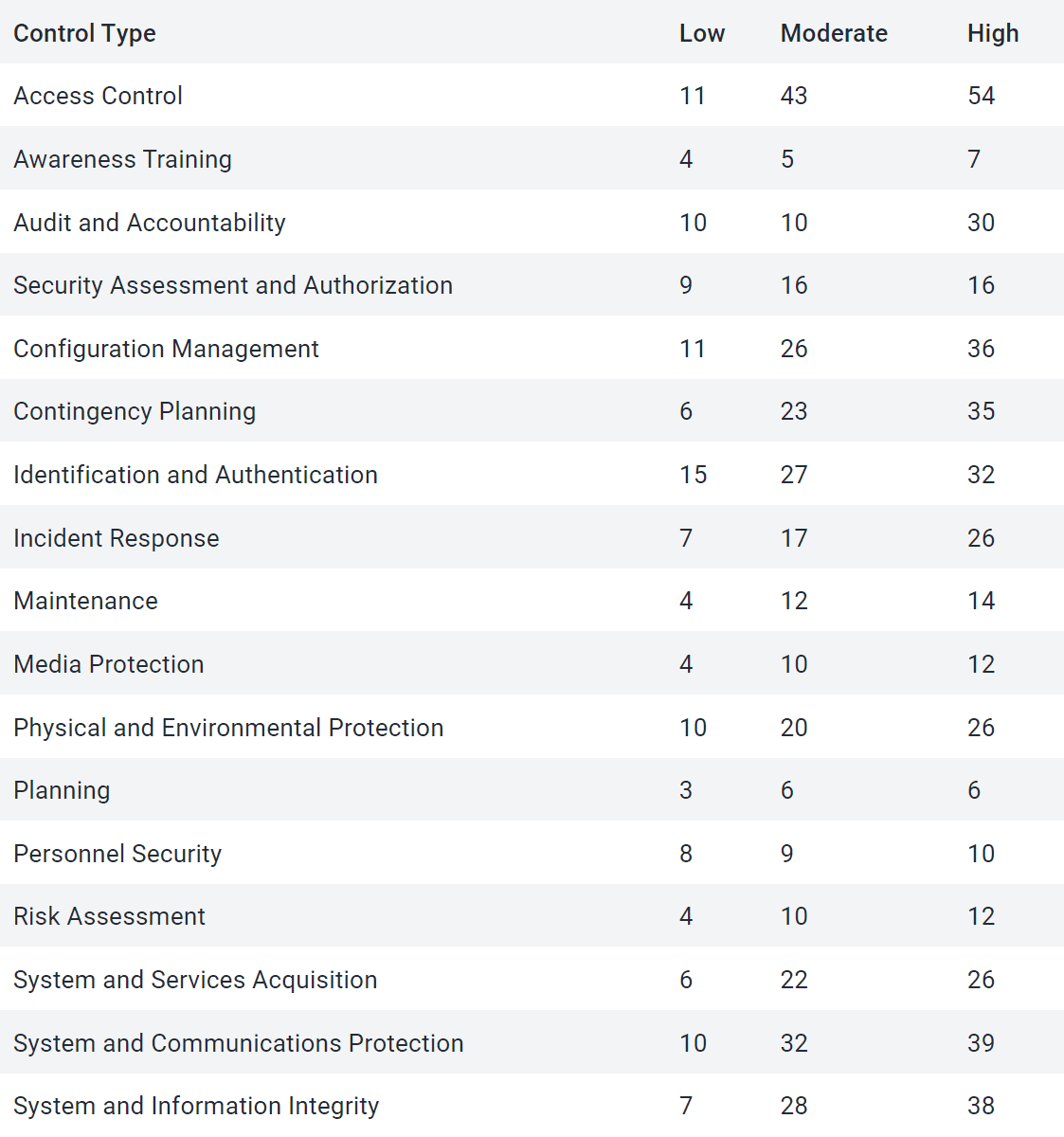
Why Is Navigating Federal Cybersecurity Standards Important for Government Contracts?
Navigating federal cybersecurity standards is essential for securing government contracts for several reasons. Primarily, these standards ensure that sensitive data is adequately protected, reducing the risk of breaches that could compromise national security.
Classifying Risks: The Framework
Federal cybersecurity guidelines classify cloud services into three distinct impact levels—Low, Moderate, and High—based on the potential risks associated with data exposure.
Low Impact: Involves the management of non-sensitive public information.
Moderate Impact: Encompasses sensitive data that, while unclassified, still requires stringent protection.
High Impact: Involves the handling of operations that are critical to national security.
By understanding this classification, providers can tailor their security measures to aligned risk levels, ensuring they meet federal standards effectively.
Compliance and Competitive Edge
For organizations, adherence to these standards isn't just a matter of compliance; it's a way to gain a competitive edge. Companies that align with federal requirements demonstrate their commitment to data security, which can enhance their reputability. It also signifies preparedness to protect critical data, offering a pivotal advantage in securing government contracts. Failure to comply, on the other hand, can result in disqualification from lucrative bidding opportunities. Learn more about what FedRAMP certification could mean for you company.
Ensuring Proper Security Protocols
Compliance necessitates a comprehensive assessment of systems to identify gaps and implement necessary security controls. Organizations might need to adjust their operations to meet the required standards, implementing specific measures to align with lower impact thresholds, if necessary.
How FedRAMP Handles Critical Infrastructure and National Security
FedRAMP plays a crucial role in the protection of critical infrastructure and national security by ensuring that cloud services meet stringent security standards. Let's delve into how FedRAMP achieves this:
Defining High-Impact Services
High-impact services are those essential to the functioning and safety of various key sectors, such as:
Law enforcement
Emergency and healthcare services
Financial and governmental systems
Disruptions in these areas can have widespread consequences, including economic turmoil and threats to public safety, even resulting in potential loss of life.
Security Considerations
1. Confidentiality
FedRAMP ensures that unauthorized access to sensitive information is minimized. A breach in confidentiality could severely harm operations, assets, and individuals, making it imperative that stringent measures are in place.
2. Integrity
Protecting the integrity of data is vital. Unauthorized data changes could have catastrophic effects, and FedRAMP's protocols are designed to prevent such occurrences, maintaining trust in the system.
3. Availability
Ensuring that essential data is accessible to authorized users when needed is crucial. FedRAMP guards against disruptions that could impact operations significantly.
Protecting Critical Information
The high standard required under FedRAMP for classifying and securing information means that some data is so sensitive it’s handled internally rather than through third-party cloud providers. For example:
Controlled Unclassified Information (CUI): Most high-impact data handled by FedRAMP-certified providers falls under this category. It's vital to security, yet classified data requires stricter handling.
Beyond CUI: Truly classified information demands even more stringent protocols, often involving secure, dedicated systems and personnel with special clearance levels, ensuring this data's integrity and confidentiality.
Government Strategies
To address these needs, the government often prefers engineering custom secure systems for the most sensitive data, rather than relying on external services, to ensure maximum security.
By adhering to robust standards, FedRAMP plays an essential role in safeguarding critical infrastructure and enhancing national security, ensuring these crucial systems remain secure and operational.
Conclusion
In essence, mastering federal cybersecurity standards is not just a bureaucratic hurdle; it is a foundational requirement for any enterprise aiming to enter or maintain a presence in the government contracting space. It ensures the security and integrity of significant operations and data, safeguarding against potential threats and maintaining national security.
In the end, this will redound to benefits to your organization regarding savings in resources, time, and cost, enhancement of real-time security, improved re-utilization of current security assessment across organizations, enhance transparency, ensure uniformity in approaches to risk-based management, and enrich the authorization process of federal security.
By knowing exactly the kind of data your organization is handling and the kind of protection these data need, you can best determine whether you will require complying to FedRAMP's low, moderate, or high-security base lines.







