Published on: May 10, 2017
4-Step Guide to Performing an ISO 27001 Risk Analysis
Performing a risk assessment is a central part of the ISO 27001 process directed to implementing an ISMS (Information Security Management System). How could you protect any sort of environment without being fully aware of impending threats, the exposition level, and variables such as the likelihood of occurrence and estimated level of impact?
Understanding all those factors and how they compare to the risk appetite of your company is a complex job, but it should enable you to select proper controls, based not on guesswork, but on empirical evidence. This process results in not only ineffective protection but also a cost-effective approach: It allows you to direct your efforts and resources to implement countermeasures that are fit to your specific scenario, protecting what really matters. At the end of the day that is what security is all about.
Before performing a risk assessment, a few questions must be answered:
What is the best method?
What tasks are necessary?
What should be the final product?
What should I do after the risk assessment?
The answer to all those questions is addressed by ISO 27001 and, in even more details, the ISO 27005 standard. The process itself is quite simple:
Step 1: Understanding Your Context
One common mistake performed by first-time risk analysts is providing the same protection level to all assets and information. Good security management means protecting what really matters, and that is the reason why understanding the context of your organization is an essential task.
If your organization is going for an ISO 27001 certification, your ISMS scope is probably mapped, so it should be simple enough to identify all relevant information regarding the context of your risk management. Other than that, your focus should be on defining the purpose of your information security risk management process, including its scope and boundaries. It should be well aligned to your organization strategy, for instance, like complying with a specific legislation such as Sarbanes-Oxley (SOX) or the General Data Protection Regulation (GDPR).
The important thing to understand is the fact that each company context is unique, and so should be your risk assessment approach. This should enable you to define the basic criteria that will be used during the assessment.
Step 2: Risk Identification
The first actual step of a risk assessment is identifying the risks. The idea is to list events that may cause potential damage to your organization, and have a clear understanding of how, where and why this loss may occur.
A practical approach is identifying all assets that fall within your scope and ensure you have sufficient information for a proper analysis. Again, this is a context driven action, but some basic information may include the type of asset, its owner and the value it represents for your company.
Once you have the assets list, the next action is understanding the threats and their respective sources. A simple yet effective approach is organizing threats into different categories such as adversarial (i.e. insiders/outsiders, cybercriminals, competitors), accidental (i.e. erroneous actions by users or even privileged users/administrators), structural (i.e. equipment failures, software errors) or environmental (i.e. natural disasters, failure of critical structure outside organization control).
You can gather this information from incident reports, talking with asset owners, or even using threat catalogues. Using a professional risk assessment tool can be quite effective and streamline the process.
Alternatively, you can take a scenario based risk approach, which can identify risks using the experiences of your internal team through risk identification workshops, interviews, questionnaires, or collecting information from past incident reports.
StandardFusion supports both asset-based and scenario-based risk methodologies. Every instance comes with over 100 asset templates, mapped to over 170 various threats. Using StandardFusion, identification of your assets is as simple as going through the asset templates and identifying what is important to you.
At this point, you should have a complete list of risks organized by type and source and plan to identify any existing security countermeasure or controls that are already implemented. This should help to avoid unnecessary work or even the duplication of controls and will provide evidence that will be the basis for understanding the current protection level. One thing to consider when identifying mitigating controls is to also ensure that the existing control is actually working as expected, otherwise, you may end up with a false sense of security.
Another very important action is identifying the vulnerabilities that may be exploited by threats and cause damage to assets. Vulnerabilities often come in several brands, including organizational errors, failures to follow defined processes/procedures, human-based problems (i.e. lack of training/awareness), environmental issues (i.e. improper Heating, ventilation and air conditioning (HVAC)) and the ever so present technical problems (i.e. operational system vulnerabilities, lack of proper malware controls). Using risk management software like StandardFusion can be of immense value and save you time and effort.
The final risk identification step is defining the impact level that may arise from the loss of information security primary aspects: Confidentiality, Integrity or Availability. This should be based on a profound analysis of the information you have collected so far and be aligned to the context of your organization. Impacts must be represented in terms that are pertinent to your scenario: The loss of operational efficiency, missed business opportunities, damage to reputation, legal issues and financial damage. The key to success is sorting out what really matters to your organization.
Step 3: Risk Analysis
Your risk analysis will fall into two basic categories: it will be either quantitative or qualitative.
Using the quantitative approach involves a statistical study of records such as incidents, real impacts and any other pertinent information that you have registered over the years. The results are presented using a numerical scale and have the advantage of having little room for subjectivity. Do not be mistaken, a quantitative analysis is actually pretty helpful, but it is entirely dependent on the level of historical data you have available, meaning if you do not have enough information, it is not practical to use the quantitative approach.
For most organizations a qualitative methodology will be simpler to implement and provide sufficient information for risk treatment. A qualitative analysis uses a scale based on qualifying attributes that describe the magnitude of both potential impacts and the likelihood of occurrence. For example, you can adopt a scale that will classify risks as very low, low, moderate, high and very high. That may sound subjective, but that is the point. During a qualitative analysis, a certain level of subjectivity is accepted, provided the team performing it has sufficient experience and the analysis itself is based on empirical data.
Once you have selected the methodology that best suits your needs, you should be able to calculate the level of impact and likelihood of occurrence and create a risk estimation.
Presuming you selected a qualitative approach, it is very easy to create a risk matrix such as this one:

If you decided to go for a quantitative analysis, you should end up with something like this:
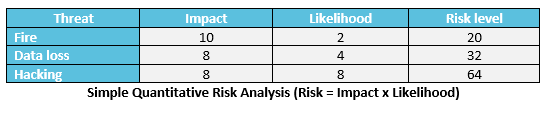
If done right, independent on the chosen methodology, the final result of your risk analysis should be a clear view of the level of each mapped risk. And this is the basis for the final step of our risk assessment.
Step 4: Risk Evaluation
So, now that you know the risk levels, it is time check how they compare to the evaluation criteria. Based on the context of your organization you should define what needs to be treated and what can be accepted as it is. This point is entirely context-driven, for example on a quantitative approach the loss of a million dollars can either be something perfectly acceptable or put you out of business, it all depends on the nature of your company and how big is your risk appetite: How much of an impact can you absorb, without it becoming a business show-stopper?
Each risk that causes an impact that goes beyond what has been defined as acceptable should be treated, and that is the final result of your risk assessment, a list of prioritized risks, based on your context and pertinent scenarios. That is more than sufficient information to form the basis of a Risk Treatment Plan, the next step on your risk management process.







